In June, a new threat has appeared in the cyber world. If you regularly read about cyber threats, you must have heard of the infamous Locky ransomware. Well, it seems it has a successor. It’s called the Zepto ransomware and it has been infecting computers all around. When it infects your computer, it encrypts your files using the RSA-2048 and AES-128 ciphers and attaches the .zepto file extension, hence the name Zepto ransomware. When it has your files at its mercy, it will ask you to pay a certain amount of money in Bitcoins. Sounds horrible, right? The worst part is, getting infected by Zepto ransomware is very easy, it happens with a click of a button.
Spam email has been a popular way to spread ransomware for a very long time now. People still do not take the threat of potential data loss seriously and carelessly open spam emails. This can lead to ransomware making home on your computer. Zepto ransomware spreads that way too. Since it has appeared, users around the world have been getting spam emails with attachments from seemingly legit senders and when they open the attachment, they find that the Zepto ransomware downloads onto their computer and locks their files.
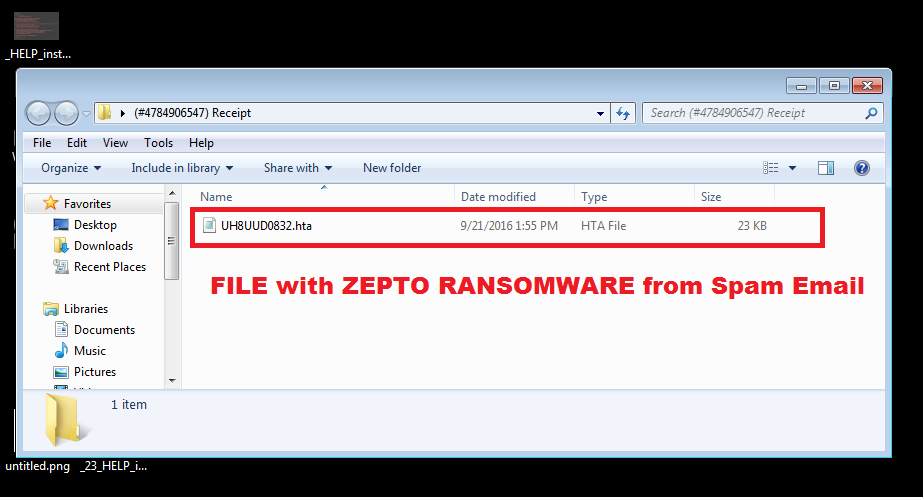
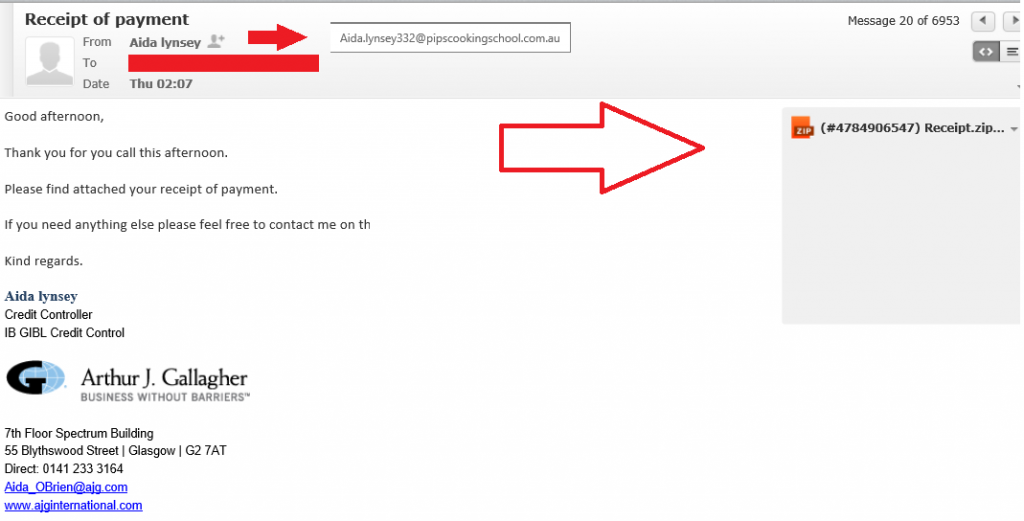
The way it happens is Zepto ransomware developers infect a file with their creation and send it to unsuspecting users. The email will contain a zip file attachment with a HTA file in it and an official looking text. One such example:
Good afternoon,
Thank you for you call this afternoon.
Please find attached your receipt of payment.
If you need anything else please feel free to contact me on the details below.
Kind regards.Aida lynsey
Credit Controller
IB GIBL Credit Control
It uses polite language, has a name at the bottom and although it has a few grammatical mistakes, it seems to be from a legit company. Looks pretty real, right? Well, it’s not. This is a very common technique to convince people to download the infected attachment. By pretending to be an official company or maybe a government organization it makes people not doubt the legitimacy of the email. Obviously, not every spam email sent by Zepto ransomware developers will be the same but there are simple ways to determine whether the email is legit or not. In the case of the provided email example, ask yourself, do you remember making a phone call to the company? Have you even heard of this company? Also, a simple Google search would make it clear that this is indeed a virus. If it causes any doubts, you should not open it, no matter how tempting it is.
Zepto ransomware is a horrible virus and you really do not want it infecting your computer. Malware researchers are yet to release the decryption key, which basically means you’ll end up loosing your files if you get infected. Paying the ransom rarely helps, too. Most ransomware developers just ignore the victims after the payment has been made. If you want to avoid Zepto ransomware and other similar threats, be cautious and do not disregard the possibility of an email containing ransomware.
The battle is over for these ransomware threats. If you have been infected with one of these types of ransomware click on the link under its name and it will lead you to a decryption tool:
- WildFire
- Chimera
- Xorist
- TeslaCrypt
- Shade
- CoinVault
- Rannoh Rakhni