The “I’ve Got Access To Your Smartphone” email falls into the sextortion email category. The email is a classic example of a sextortion scam email. It falsely claims that users’ smartphones have been infected with malware, which supposedly allowed its operators to create a video of the user watching pornography. The contents are completely false so users can ignore the email.
Nowadays, sextortion email scams are very common, and most users will have received at least one. They usually land in the spam folder so users usually don’t even notice them. The majority of sextortion emails are very similar to one another, even when different scammer groups operate them. And the fact that they are all fake is just one thing they all have in common.
When looking at these emails with a clear head, they’re not very convincing. However, if users become alarmed, sextortion email content may seem very scary. Scammers also use scare tactics to make users anxious and pressure them into making rash decisions. Scammers use degrading language and try to embarrass the recipient by mocking their supposed pornography viewing habits. The threat to expose users’ explicit videos to contacts is also an effective tactic.
Sextortion emails always try to catch users’ attention with alarming subject lines like “I’ve Got Access To Your Smartphone”. If users open these emails, they are greeted with messages explaining that the sender has hacked their devices, in this case, their smartphones. The sender explains that users’ devices got infected with malware after they visited adult websites. The malware supposedly gave its operators complete access to the device, including contact information and the ability to turn the microphone/camera on and off.
According to the sender, when they noticed the recipient visiting pornography websites, they decided to make a video of them watching it. They threaten to send the video to all contacts unless users agree to pay $1,000.
It goes without saying that the email contents are completely fake. There is no malware on the computer, nor is there a video of users watching pornography.
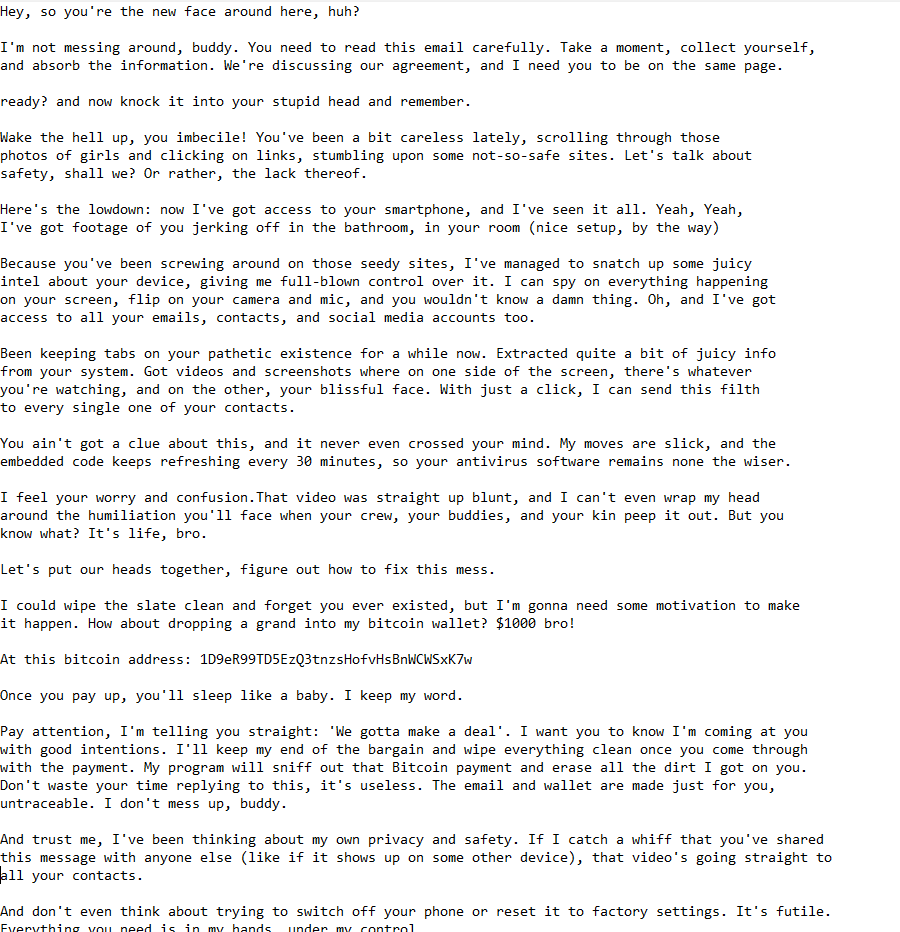
Below is the full “I’ve Got Access To Your Smartphone” email scam:
Hey, so you’re the new face around here, huh?
I’m not messing around, buddy. You need to read this email carefully. Take a moment, collect yourself, and absorb the information. We’re discussing our agreement, and I need you to be on the same page.
ready? and now knock it into your stupid head and remember.
Wake the hell up, you imbecile! You’ve been a bit careless lately, scrolling through those photos of girls and clicking on links, stumbling upon some not-so-safe sites. Let’s talk about safety, shall we? Or rather, the lack thereof.
Here’s the lowdown: now I’ve got access to your smartphone, and I’ve seen it all. Yeah, Yeah, I’ve got footage of you jerking off in the bathroom, in your room (nice setup, by the way)
Because you’ve been screwing around on those seedy sites, I’ve managed to snatch up some juicy intel about your device, giving me full-blown control over it. I can spy on everything happening on your screen, flip on your camera and mic, and you wouldn’t know a damn thing. Oh, and I’ve got access to all your emails, contacts, and social media accounts too.
Been keeping tabs on your pathetic existence for a while now. Extracted quite a bit of juicy info from your system. Got videos and screenshots where on one side of the screen, there’s whatever you’re watching, and on the other, your blissful face. With just a click, I can send this filth to every single one of your contacts.
You ain’t got a clue about this, and it never even crossed your mind. My moves are slick, and the embedded code keeps refreshing every 30 minutes, so your antivirus software remains none the wiser.
I feel your worry and confusion.That video was straight up blunt, and I can’t even wrap my head around the humiliation you’ll face when your crew, your buddies, and your kin peep it out. But you know what? It’s life, bro.
Let’s put our heads together, figure out how to fix this mess.
I could wipe the slate clean and forget you ever existed, but I’m gonna need some motivation to make it happen. How about dropping a grand into my bitcoin wallet? $1000 bro!
At this bitcoin address: 1D9eR99TD5EzQ3tnzsHofvHsBnWCWSxK7w
Once you pay up, you’ll sleep like a baby. I keep my word.
Pay attention, I’m telling you straight: ‘We gotta make a deal’. I want you to know I’m coming at you with good intentions. I’ll keep my end of the bargain and wipe everything clean once you come through with the payment. My program will sniff out that Bitcoin payment and erase all the dirt I got on you. Don’t waste your time replying to this, it’s useless. The email and wallet are made just for you, untraceable. I don’t mess up, buddy.
And trust me, I’ve been thinking about my own privacy and safety. If I catch a whiff that you’ve shared this message with anyone else (like if it shows up on some other device), that video’s going straight to all your contacts.
And don’t even think about trying to switch off your phone or reset it to factory settings. It’s futile. Everything you need is in my hands, under my control.
You got 5-6 hours to get it sorted. I’m giving you plenty of time to think it over and do what’s right by our agreement. I’m expecting that payment.
Don’t take it personally. Think of it as a little life advice and be more vigilant in the future.
Honestly, those online tips about covering your camera aren’t as useless as they seem.
Good luck with that. Farewell.
Why were you targeted with a sextortion email?
Users who receive sextortion emails may wonder why they received the emails if not because their devices are infected. The reason users receive sextortion emails is because their email addresses have been leaked. Unfortunately, a lot of services have inadequate security, which means that all kinds of information can be stolen if a cyber attack were to happen. Stolen data is usually sold on hacker forums, where other cybercriminals buy it to use for their malicious activities (e.g. sextortion email scams). Users can use haveibeenpwned to check whether their email addresses have been leaked. If your email address has been leaked, there’s not much you can do but you can at least be more cautious with unsolicited emails, especially ones that contain links or attachments.
In order to appear more convincing, some scammers also include users’ passwords in sextortion emails. For users who are not familiar with sextortion scam emails, the emails may seem significantly more credible if their passwords are revealed. Again, users may wonder how would the sender know their passwords if not because of malware on their computers. However, there’s a simple explanation for this. Passwords are obtained by cybercriminals in the same way as email addresses. A lot of services store passwords in plain text, which means passwords would be stolen during a cyberattack. They are then sold on hacker forums for other cybercriminals to buy.
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.