The “I Have To Share Bad News With You” email falls into the sextortion scam email category. It’s a generic scam email that threatens to release a non-existent video of the recipient watching pornography. The email is nothing more than a scam.
This “I Have To Share Bad News With You” email scam is part of one of many sextortion scam campaigns that aim to scare people into paying hundreds of dollars in exchange for not releasing explicit videos that don’t actually exist.
The email starts with an alarming claim that the recipient’s internet activities have been tracked by the sender. The “hacker” proceeds to explain that they purchased access to the recipient’s email account from other hackers, which somehow allowed them to infect their device with a trojan. The trojan supposedly gave the “hacker” access to the computer, including the ability to control the microphone and camera. The sender claims that this allowed them to create a video of the recipient watching pornography. They also claim to have stolen all contacts and threaten to send the video to all of them unless the recipient agrees to pay $950 in Bitcoin. It goes without saying that paying would be a waste of money because this is nothing more than a scam email.
These sextortion emails are surprisingly effective and many users have paid. That is because the emails use various scare tactics. Sextortion emails are written in very mocking tones, with senders often shaming recipients for their supposed pornography-watching habits. The threat to send explicit videos to recipients’ contacts is also effective.
Every single one of these types of emails is fake. If you ever encounter one, you can simply ignore the contents and delete it from your inbox.
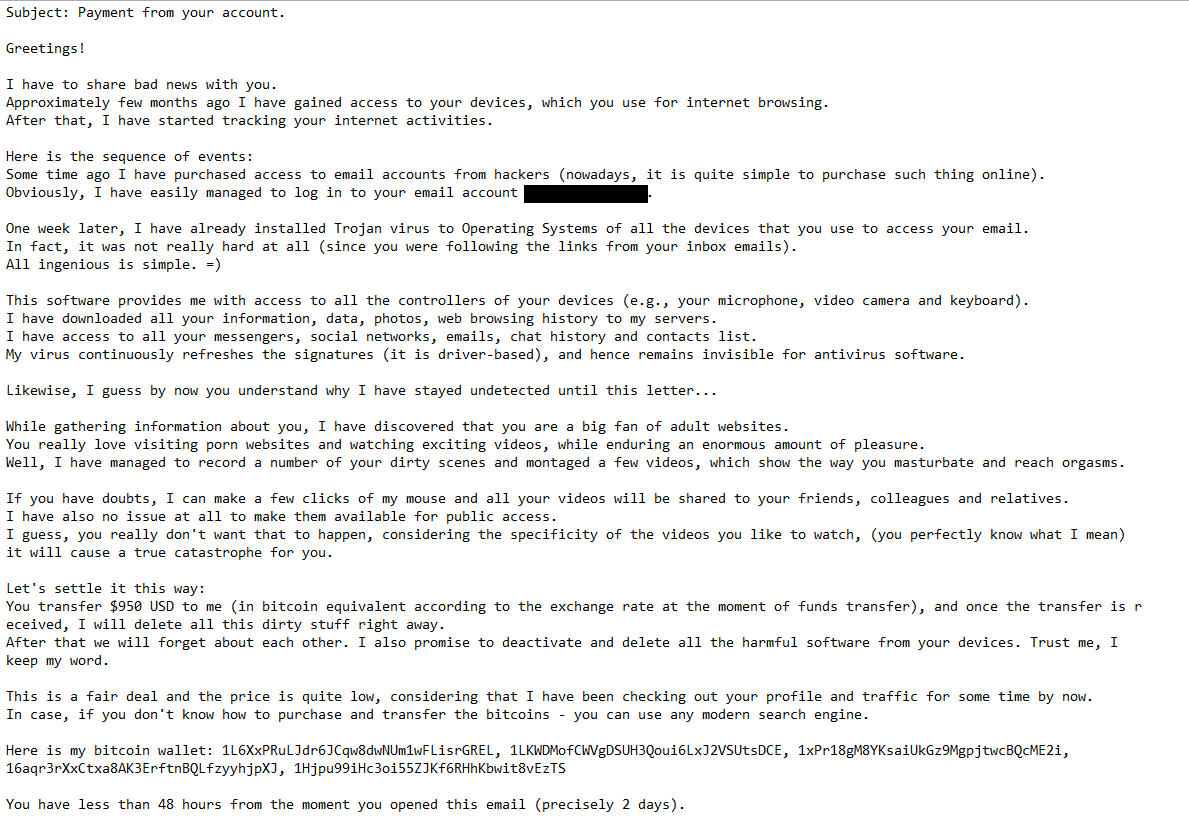
Below is the full text from the “I Have To Share Bad News With You” email scam:
Subject: Payment from your account.
Greetings!
I have to share bad news with you.
Approximately few months ago I have gained access to your devices, which you use for internet browsing.
After that, I have started tracking your internet activities.Here is the sequence of events:
Some time ago I have purchased access to email accounts from hackers (nowadays, it is quite simple to purchase such thing online).
Obviously, I have easily managed to log in to your email account (-).One week later, I have already installed Trojan virus to Operating Systems of all the devices that you use to access your email.
In fact, it was not really hard at all (since you were following the links from your inbox emails).
All ingenious is simple. =)This software provides me with access to all the controllers of your devices (e.g., your microphone, video camera and keyboard).
I have downloaded all your information, data, photos, web browsing history to my servers.
I have access to all your messengers, social networks, emails, chat history and contacts list.
My virus continuously refreshes the signatures (it is driver-based), and hence remains invisible for antivirus software.Likewise, I guess by now you understand why I have stayed undetected until this letter…
While gathering information about you, I have discovered that you are a big fan of adult websites.
You really love visiting porn websites and watching exciting videos, while enduring an enormous amount of pleasure.
Well, I have managed to record a number of your dirty scenes and montaged a few videos, which show the way you masturbate and reach orgasms.If you have doubts, I can make a few clicks of my mouse and all your videos will be shared to your friends, colleagues and relatives.
I have also no issue at all to make them available for public access.
I guess, you really don’t want that to happen, considering the specificity of the videos you like to watch, (you perfectly know what I mean) it will cause a true catastrophe for you.Let’s settle it this way:
You transfer $950 USD to me (in bitcoin equivalent according to the exchange rate at the moment of funds transfer), and once the transfer is received, I will delete all this dirty stuff right away.
After that we will forget about each other. I also promise to deactivate and delete all the harmful software from your devices. Trust me, I keep my word.This is a fair deal and the price is quite low, considering that I have been checking out your profile and traffic for some time by now.
In case, if you don’t know how to purchase and transfer the bitcoins – you can use any modern search engine.Here is my bitcoin wallet:
You have less than 48 hours from the moment you opened this email (precisely 2 days).
Things you need to avoid from doing:
*Do not reply me (I have created this email inside your inbox and generated the return address).
*Do not try to contact police and other security services. In addition, forget about telling this to you friends. If I discover that (as you can see, it is really not so hard, considering that I control all your systems) – your video will be shared to public right away.
*Don’t try to find me – it is absolutely pointless. All the cryptocurrency transactions are anonymous.
*Don’t try to reinstall the OS on your devices or throw them away. It is pointless as well, since all the videos have already been saved at remote servers.Things you don’t need to worry about:
*That I won’t be able to receive your funds transfer.
– Don’t worry, I will see it right away, once you complete the transfer, since I continuously track all your activities (my trojan virus has got a remote-control feature, something like TeamViewer).
*That I will share your videos anyway after you complete the funds transfer.
– Trust me, I have no point to continue creating troubles in your life. If I really wanted that, I would do it long time ago!Everything will be done in a fair manner!
One more thing… Don’t get caught in similar kind of situations anymore in future!
My advice – keep changing all your passwords on a frequent basis
How did scammers get your email address?
Unfortunately, receiving a sextortion email likely means your email address has been leaked. Users’ personal information like email addresses is leaked all the time by companies that do not have adequate security and suffer a cyber attack. Stolen email addresses are sold on hacker forums for other malicious actors to purchase. You can check whether your email address has been leaked on haveibeenpwned. There’s not much you can do if it has but you can at least be cautious with unsolicited emails, especially if they contain attachments or links.
Some sextortion emails also reveal information like users’ passwords and phone numbers. This is an effective scare tactic that can often force many users to pay. If users have never encountered sextortion scam emails before, they would be confused as to how the senders managed to obtain their personal information if not because of malware on their computers. While seeing your password may seem scary, there’s a simple explanation for this. Passwords and other personal data like phone numbers are obtained by scammers much the same way as email addresses, from hacker forums. Email addresses are not the only data that is leaked by companies. If, for example, a service stores passwords in plain text, they would easily be stolen during a cyberattack. They would then be sold on hacker forums.
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.