“Hacker Who Has Access To Your Operating System” email is a scam email that falls into the sextortion scam category. The sender claims to have hacked the recipient’s computer and threatens to release an explicit video of them if they do not agree to pay $500 in Bitcoins. The contents of the email are fake, and the email can be ignored.
Sextortion email scams have become very common, with most users having received at least one. They are all very similar to one another, even if they’re operated by different scammers. They’re also all fake, no matter how realistic the threats seem.
Sextortion email scams use various scare tactics to make users anxious and more susceptible to the deception. This is done by using mocking language, trying to embarrass the recipient by mentioning their supposed pornography viewing habits, and with threats to expose users’ explicit videos to contacts.
Sextortion emails first try to catch users’ attention with subject lines like “Security Alert. Your accounts were hacked by a criminal group”. If users open this particular “Hacker Who Has Access To Your Operating System” email, they will be greeted with a message explaining that the sender has hacked their operating systems. The sender introduces themselves as a hacker and claims that the recipient’s computer was infected with malware after they visited an adult website. The malware supposedly gave them complete access to the device, which allowed them to turn the camera/microphone on and off.
The sender claims to have made a video of the recipient watching pornography and threatens to release it publicly if they do not agree to pay $500 in Bitcoin to one of the provided wallet addresses. They also threaten to send the video to all contacts.
While the email may seem alarming, all of its contents are fake. There is no need to pay anything.
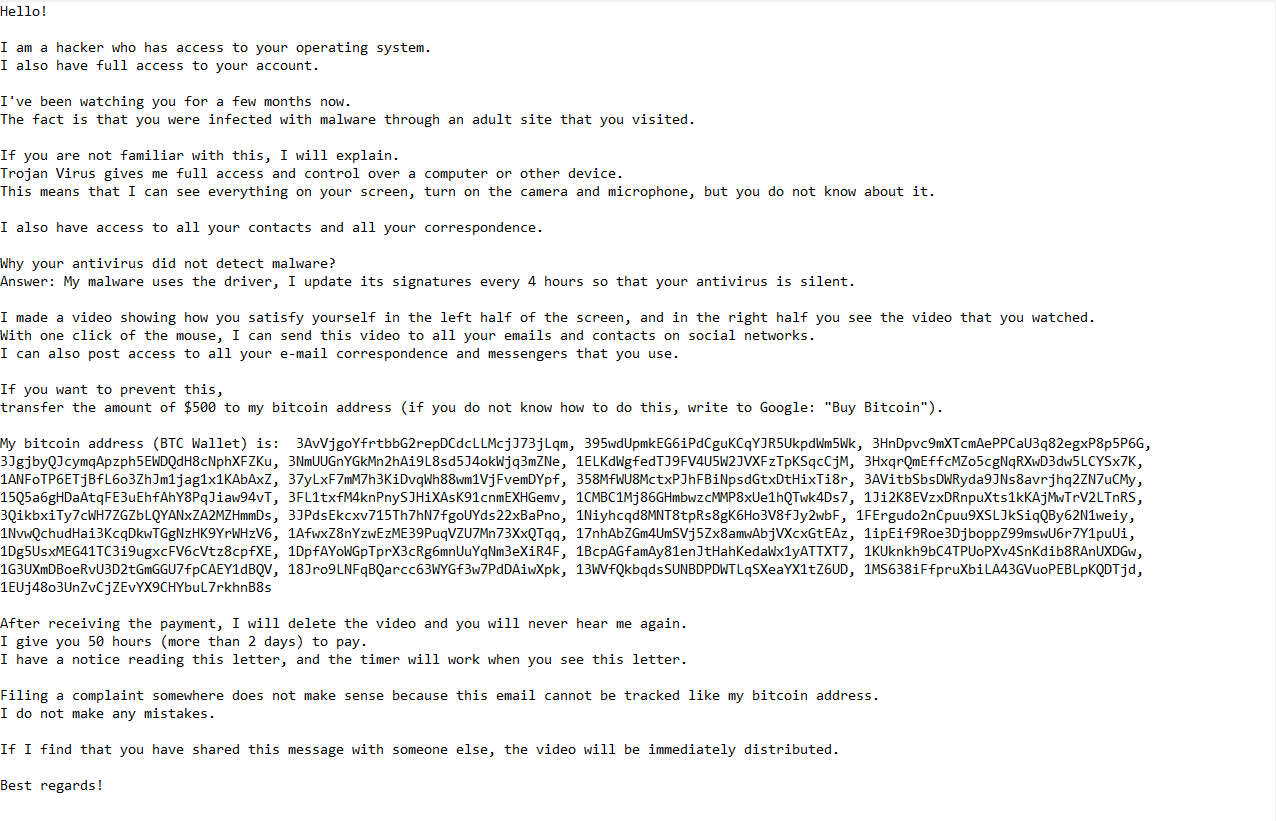
Below is the full “Hacker Who Has Access To Your Operating System” email scam:
Subject: Security Alert. Your accounts were hacked by a criminal group.
Hello!
I am a hacker who has access to your operating system.
I also have full access to your account.I’ve been watching you for a few months now.
The fact is that you were infected with malware through an adult site that you visited.If you are not familiar with this, I will explain.
Trojan Virus gives me full access and control over a computer or other device.
This means that I can see everything on your screen, turn on the camera and microphone, but you do not know about it.I also have access to all your contacts and all your correspondence.
Why your antivirus did not detect malware?
Answer: My malware uses the driver, I update its signatures every 4 hours so that your antivirus is silent.I made a video showing how you satisfy yourself in the left half of the screen, and in the right half you see the video that you watched.
With one click of the mouse, I can send this video to all your emails and contacts on social networks.
I can also post access to all your e-mail correspondence and messengers that you use.If you want to prevent this,
transfer the amount of $500 to my bitcoin address (if you do not know how to do this, write to Google: “Buy Bitcoin”).My bitcoin address (BTC Wallet) is: –
After receiving the payment, I will delete the video and you will never hear me again.
I give you 50 hours (more than 2 days) to pay.
I have a notice reading this letter, and the timer will work when you see this letter.Filing a complaint somewhere does not make sense because this email cannot be tracked like my bitcoin address.
I do not make any mistakes.If I find that you have shared this message with someone else, the video will be immediately distributed.
Best regards!
Why were you targeted with a sextortion email?
If users receive sextortion scam emails, they may wonder why they were targeted. It’s usually because their email addresses had been leaked. A lot of services have poor security, which means that if a cyber attack were to happen, users’ data could be stolen. Stolen data usually ends up on hacker forums, where other cybercriminals buy it to use for their malicious activities (e.g. sextortion email scams). Users can check whether their email address has been leaked on haveibeenpwned. There’s not much users can do if it has been leaked but they can at least be more cautious with unsolicited emails.
In an effort to appear more convincing, some sextortion emails also reveal users’ passwords. If users have not encountered a sextortion scam email before, the contents may seem much more believable if their passwords are revealed. In some users’ minds, how would the sender know their passwords if not because of malware on their computers? There’s a simple explanation for this. Passwords are obtained by cybercriminals in the same way as email addresses. Many services store passwords in plain text, which means that if they suffer a cyberattack, passwords can easily be stolen. They are then sold on hacker forums for other cybercriminals to buy.
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.