What is Nmon.exe
Nmon.exe seems to be an executable file related to the Snake, or otherwise known as Ekans ransomware. The ransomware is a particularly dangerous piece of malware that primarily targets industrial control systems (ICS), not individual machines but entire networks. Car manufacturer Honda is reportedly the latest victim to be affected by the Snake ransomware. It has reportedly caused serious disruptions in the company’s regular activities. 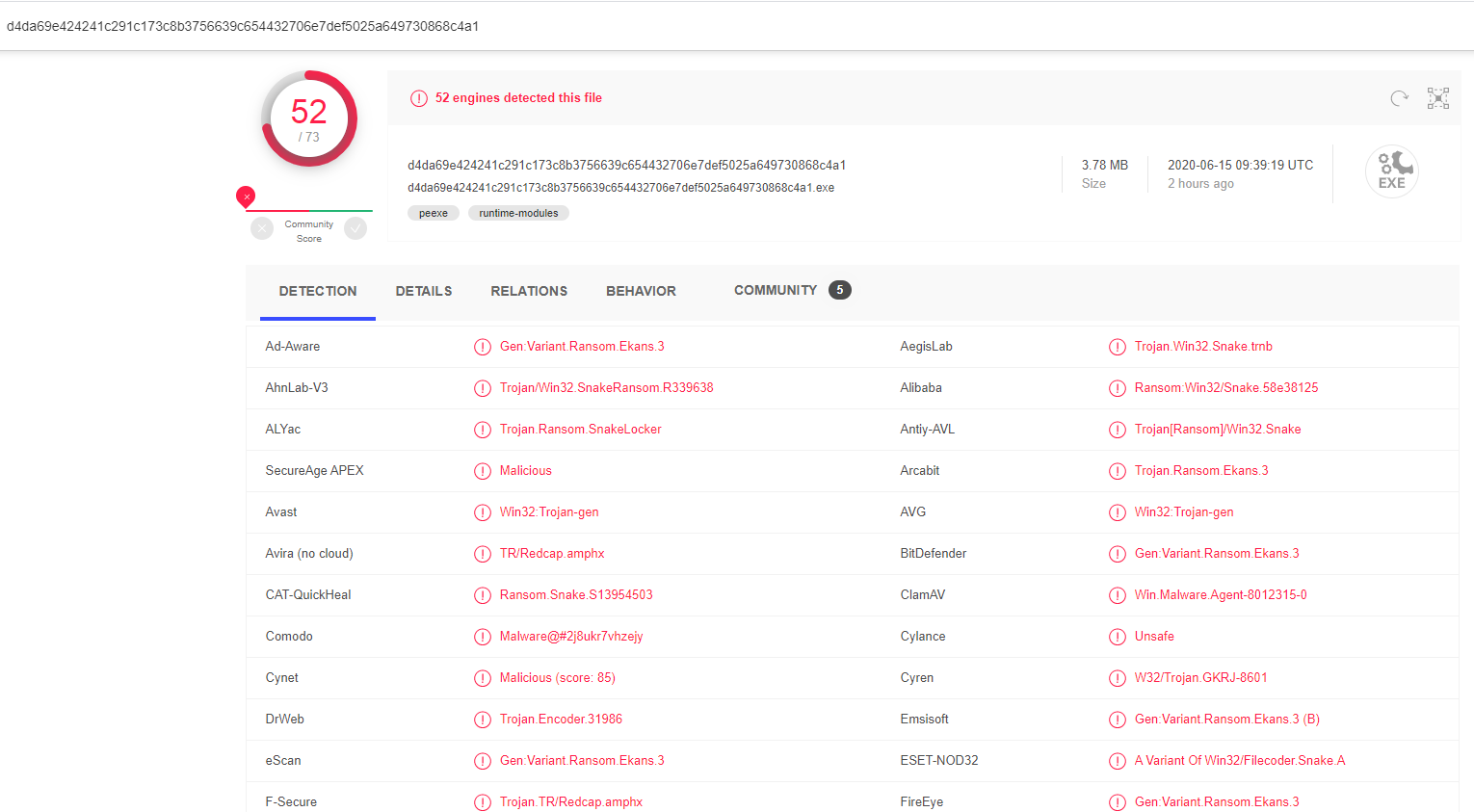
Like most ransomware, Snake malware seems to use the usual methods of infiltration, such as spam emails. Once it’s in, it terminates specific processes on a machine and deletes Volume Shadow Copies in order to prevent victims from recovering files. It then starts file encryption, after which files become inaccessible. The ransomware drops a ransom note but does not specify the amount victims need to pay to recover files, only that it’s necessary to contact the crooks behind the ransomware.
Paying the ransomware is highly discouraged by both security specialists and law enforcement because there are no guarantees that files will be decrypted. It’s not uncommon for crooks to just take off with the money. And considering that Ekans targets large companies, the ransom sum is likely to be substantial.
To remove Nmon.exe and the Snake ransomware, using anti-malware software will be necessary.
How does the ransomware spread?
According to software company Acronis, Snake ransomware enters via insecure RDP configuration. It’s primarily distributed via spam email attachments, but can also be spread via botnets, exploit packs, malicious ads, web infections, fake updates, and infected installers.
Spam email with attachments are one of the main ransomware distribution methods. Malicious files come attached to spam emails that are made to look like some kind of official correspondence from a company, bank, government agency, etc. The emails try to convince potential victims to open the attached file by claiming it’s some kind of important document. When the file is downloaded and opened, the malware can execute. In many cases, the emails have certain signs that point to it not being what it appears to be at first sight. Spam is often sent from questionable email addresses, the emails have grammar and spelling mistakes, address the receiver with generic “User/Customer/Member” greetings, etc. It’s certainly possible to differentiate legitimate emails from those carrying malware. Finally, all file attachments that come with unsolicited emails should be scanned with anti-malware software or a service like VirusTotal.
Having reliable anti-malware software installed on the system will go a long way towards protecting against malware. A lot of these security tools detect ransomware as soon as it enters and are able to prevent file encryption.
What does the ransomware do?
When the ransomware is executed, it will immediately delete Shadow Volume Copies and stop processes related to SCADA systems, virtual machines, industrial control systems, remote management tools, and network management software. Shadow Volume Copies would allow victims to recover files without paying the ransom, thus most ransomware delete them.
The ransomware then starts encrypting files, skipping those located in certain folders, such as :\Program Files. All encrypted files will have a random upper and lover case five-character string added. Once the encryption process is complete, it drops a ransom note “Fix-Your-Files.txt”. The ransom note explains that the corporate network has been breached and files encrypted. The note further clarified that the only sure way to recover files would be by purchasing the decryption tool. The note also explains that victims can send crooks up to three unimportant encrypted files as insurance that files can really be decrypted. The requested sum for the decryptor is not specified in the note, and will likely be made clear if victims contact them by email (bapcocrypt@ctemplar.com).
Victims are always advised against paying the ransom because there are no guarantees that a decryptor will be sent. And seeing that Snake ransomware targets companies instead of individual users, the requested ransom sum will likely be at least a couple of hundred thousand dollars, if not more. Paying may also lead to a repeat attack, as the cyber criminals behind this ransomware will keep in mind who is willing to pay.
Nmon.exe removal
Nmon.exe indicates the presence of Snake ransomware, which should only be removed with anti-malware software. If backup is available, it should only be accessed once all traces of the ransomware have been removed.
Offers
Download Removal Toolto scan for Nmon.exeUse our recommended removal tool to scan for Nmon.exe. Trial version of provides detection of computer threats like Nmon.exe and assists in its removal for FREE. You can delete detected registry entries, files and processes yourself or purchase a full version.
More information about SpyWarrior and Uninstall Instructions. Please review SpyWarrior EULA and Privacy Policy. SpyWarrior scanner is free. If it detects a malware, purchase its full version to remove it.

WiperSoft Review Details WiperSoft (www.wipersoft.com) is a security tool that provides real-time security from potential threats. Nowadays, many users tend to download free software from the Intern ...
Download|more


Is MacKeeper a virus? MacKeeper is not a virus, nor is it a scam. While there are various opinions about the program on the Internet, a lot of the people who so notoriously hate the program have neve ...
Download|more


While the creators of MalwareBytes anti-malware have not been in this business for long time, they make up for it with their enthusiastic approach. Statistic from such websites like CNET shows that th ...
Download|more
