Sextortion email scams on the rise
Sextortion emails, also known porn blackmail email scams, have been on the rise in the past year. Different forms of it have been around for many years but they became particularly active in 2018, with thousands of users bombarded with rather sophisticated blackmail attempts. FBI’s Internet Crime Complaint Center (IC3) reportedly received 13,000 complaints between July 1 and the beginning of August. Such emails claim that you have malware installed on your computer, and it allowed attackers to film you via webcam while you were watching a pornographic video. The emails claim that all your contacts have been stolen from the computer, and that they will all receive the video of you unless you agree to pay a certain amount of money. 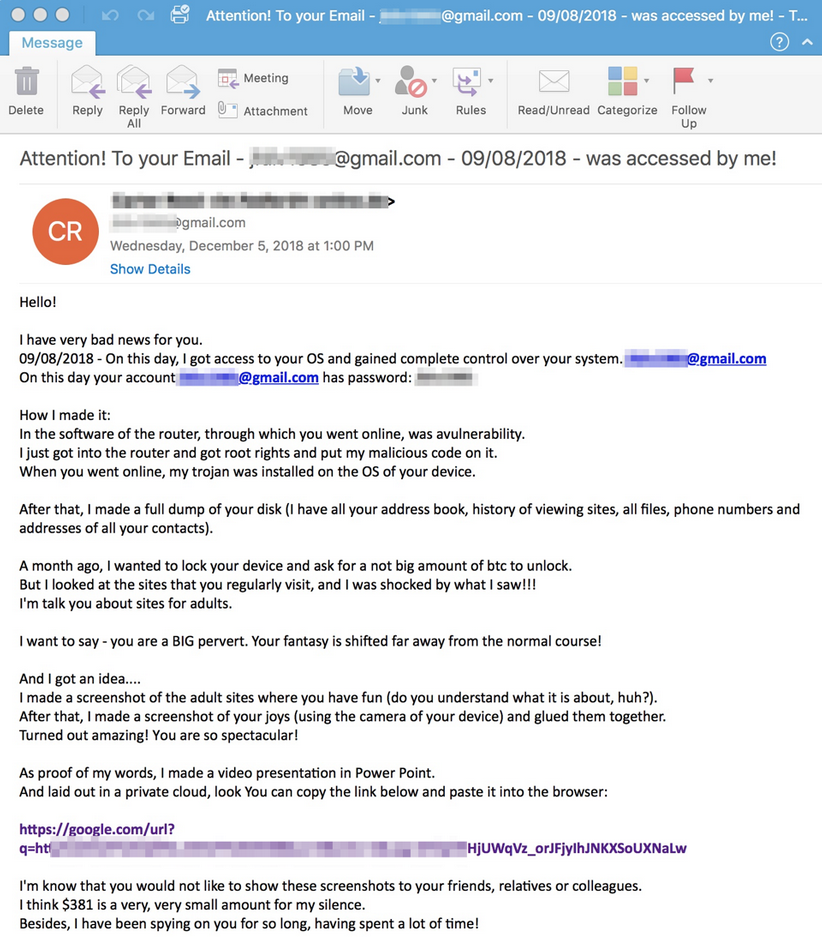
The emails all follow a certain pattern. They first try to catch your attention by displaying one of your passwords or your phone number. They then proceed to explain that when you visited a particular porn website, malware was installed on your computer. The malware then accessed your camera and filmed you while you were supposedly watching an adult video. Typically, the email says that a video showing both the video and you watching it has been made. According to the email, if you want the video to disappear, you need pay. The sum demanded is generally around a couple of thousand dollars. Since said video does not exist, it goes without saying that you don’t need to pay anything.
Because pornography is a very sensitive subject, people become easily alarmed. All the what ifs lead to many users agreeing to pay the requested sums, even when they know they have not visited any adult websites.
In recent days, security researchers from software company Proofpoint have noticed that some of these sextortion scams no longer only demand money directly, but also trick users into installing data-stealing Trojans and file-locking GandCrab ransomware.
Emails saying I know your password spread GandCrab ransomware
This new email campaign starts off similarly to the above described one. It starts off by revealing your email and password, and then goes on to explain that malware was installed on your computer. The scammer states, in a rather condescending tone and weird English, that initially, he/she did not have the intention of blackmailing you but noticed that you supposedly visited adult websites and watched rather perverse videos. The scammer than got the idea to make a screenshot of a scene in the video and you watching that video. Supposedly, all your contacts were also stolen, and unless you agree to pay, they will all receive the screenshots. Up until this point, this porn blackmail email with password looks very much like previous campaigns, but near the end it provides a link to the screenshots as proof. Proofpoint provides an example of such an email here.
If you were to click on the link, it would take lead you to AZORult malware, which would then install GandCrab 5.0.4 ransomware. The ransomware would encrypt your files and request 0.15 Bitcoin (around $500). The version of GandCrab ransomware that is spread via these sextortion email is not currently decryptable.
How do sextortion scammers obtain passwords and phone numbers?
In case it has not been made clear yet, these sextortion emails are scams, nothing more. No malware was installed if/when you visited an adult website, and the sender of the email certainly does not have a video or screenshots of you. However, the reason these porn blackmail emails are more likely to succeed compared to other campaigns is users’ passwords/phone numbers. A familiar password or a phone number goes a long way towards convincing users that it’s legitimate.
So if the emails are fake, how do scammers obtain correct passwords and phone numbers? An important question with a very simple answer. Data breaches. If you get such an email and the password is actually one you have used before, the service you used the password for was likely hacked and users’ data was stolen. It is the same with phone numbers as well. The scammers behind these sextortion email campaigns then bought the password/phone number along with your email.
If you have received this email and the password displayed is one you actually use, you need to change it immediately. The more complex it is, the better. And make sure it is unique as passwords should never be reused. Furthermore, never click on links you get in such emails, as they will certainly lead either malware or a phishing attempt.