Malware researcher xXToffeeXx has stumbled upon a new ransomware that spreads by hacking remote desktop services. The ransomware, called RSAUtil, is currently undecryptable which means there is no way to decrypt files for free. Despite this, paying the ransom is not recommended.
As is typical for ransomware, once it encrypts your files, it will demand that you pay. Hacking remote desktop services is not usual for ransomware and more basic methods, such as spam emails or fake updates, are usually used. In the case of RSAUtil, it will place a package of files on your computer that will execute the ransomware. There is a variety of files that are found in the package.
A CMD file will make sure to clear all event logs which removes all traces of the infection patterns. Two files, DontSleep_x64.exe and DontSleep_x64.ini, will prevent your computer from going to sleep so the encryption is not interrupted. The ransom note is in the How_return_files.txt file and it will be placed in all folders that have encrypted files. Image.jpg is the image that would be set as your desktop. It contains a message saying all your files are encrypted and implies that you should email the developer.
config.cfg is the file that is responsible for the encryption. It checks whether your computer has already been encrypted, sets the ID, the email, the ransom note, file extensions added to encrypted files and the public encryption key, which is used to encrypt the files. The NE SPAT.bat file will configure numerous remote desktop service options. This file will essentially ensure that the connection to the remote desktop is not lost. To launch the ransomware, the hacker has to run the svchosts.exe file. It will search for files and encrypt them. Malware researchers note that RSAUtil ends up encrypting executable files because it has no set list of file types.
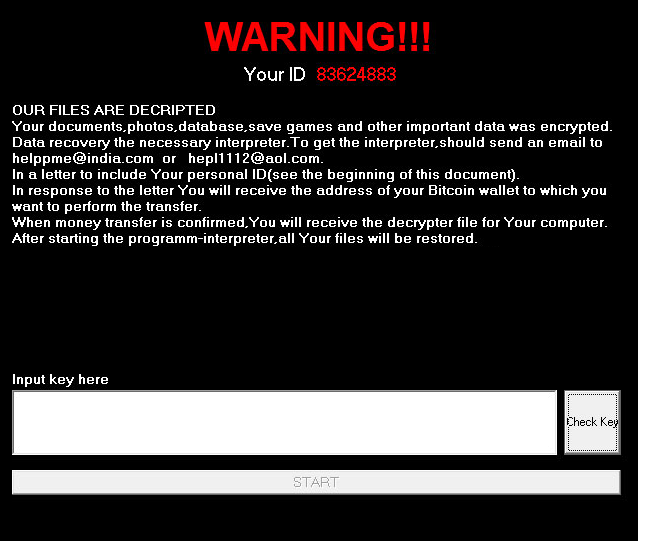
When the whole launch and encryption process is complete, the victim’s screen will be locked and a message will appear. It will display the victim’s ID and explain that files have been encrypted. Two email addresses, helppme@india.com and hepl1112@aol.com, will be given and victims are asked to use them to contact the hackers. The amount the victim would need to pay is not stated in the message and it is assumed that it would be given via email.
It is never recommended to comply with the ransom demands and pay the amount requested because you are still dealing with cyber criminals. There are many cases when users paid and still did not get a method to decrypt their files. It is usually recommended that victims invest the money into getting reliable backup so that if a similar situation happened again, there would be no need to worry about file encryption. And malware researchers may be able to develop a decryptor in the future so your files may not be lost after all.