Shadaloo ransomware is file-encrypting malware. It’s a typical ransomware infection that encrypts personal files and demands payment for their decryption. Unfortunately, only users who have backups can currently recover files for free as there is no free Shadaloo ransomware decryptor.
When the ransomware successfully infects a device, it immediately starts encrypting files. Unfortunately, it mainly targets personal files, including photos, images, videos, documents, etc. Encrypted files will have a .shadaloo extension added to them. For example, an encrypted text.txt file would become text.txt.shadaloo. You will not be able to open these files unless you first decrypt them. However, getting a decryptor is not going to be easy as the only people who currently have it are the cybercriminals operating this ransomware.
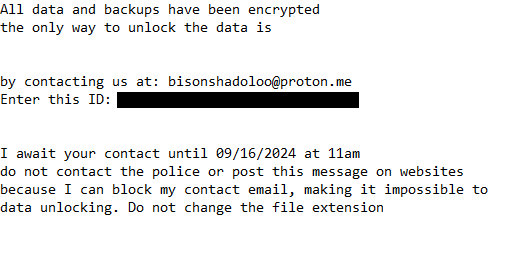
The ransomware drops a HOW TO DECRYPT FILES.txt ransom note once it’s done encrypting files. The note is brief and contains little information besides instructions that users need to contact the cybercriminals via bisonshadoloo@proton.me. The note does not mention how much the decryptor costs but it’s likely to be around $1,000.
The full Shadaloo ransomware ransom note is below:
All data and backups have been encrypted
the only way to unlock the data isby contacting us at: bisonshadoloo@proton.me
Enter this ID: –I await your contact until 09/16/2024 at 11am
do not contact the police or post this message on websites
because I can block my contact email, making it impossible to
data unlocking. Do not change the file extension
When it comes to ransomware, paying the ransom is not something we ever recommend. There are two main reasons for this. First of all, paying does not guarantee that a decryptor will be sent to you. You need to keep in mind that you are dealing with cyber criminals, and there is nothing to force them to keep their end of the deal. And they often do not. Secondly, the money you pay would go towards future criminal activities.
If you have a backup of your files, you can connect to it to start file recovery as soon as the ransomware has been removed. It’s strongly recommended to use an anti-malware program because ransomware is a complicated infection.
For users with no backups, the only option is to back up the encrypted files and occasionally check NoMoreRansom for a free Shadaloo ransomware decryptor. If a decryptor cannot be found on Shadaloo ransomware, you likely won’t find it anywhere else. You should also know that there are many fake decryptors on dubious forums and sites, and they could lead you to more infections.
How does ransomware infect a computer?
Ransomware is often distributed through email attachments, torrents, malicious ads, and links. Users who have poor browsing habits are considerably more likely to pick up malware because they take greater risks when browsing. To avoid future malware infections, you need to become familiar with how malware is distributed and develop better browsing habits.
If your email address has been leaked, you may receive emails with malicious attachments. Malicious emails mass target users so they are generally quite generic and easy to recognize as malicious. These emails are designed to look like they are sent by legitimate companies and may be disguised as order confirmations or parcel delivery notifications. However, a giveaway is often glaring grammar and spelling mistakes, which would not be present in legitimate emails sent by legitimate companies because they look unprofessional.
Another indication of a malicious email is when the sender, who should know your name, addresses you using generic words like “User,” “Member,” “Customer,” etc. You may have noticed this but legitimate companies usually use customers’ names when corresponding via email. Malicious senders resort to generic greetings because they typically have access to no more personal information than an email address.
However, it’s worth mentioning that some malicious emails may be much more sophisticated. Therefore, it’s always a good idea to scan all unsolicited email attachments with anti-malware software or VirusTotal before opening them.
Downloading from poorly regulated torrent sites is another quick way to get malware. It’s no secret that torrents for popular movies, TV series, and video games often contain malware. So using torrents to download copyrighted content is not only illegal but also risky for your computer/data.
Remove Shadaloo ransomware
Ransomware is a very complicated infection so it’s important to avoid causing additional damage to your computer by trying to remove Shadaloo ransomware manually. Make sure to use an anti-malware program.
Once Shadaloo ransomware is no longer detected, it’s safe to access your backup to start recovering your files, if you have it. If a backup is not available, you need to back up the encrypted files and wait for a free Shadaloo ransomware decryptor to be released. If it does get released, it will be available on NoMoreRansom.
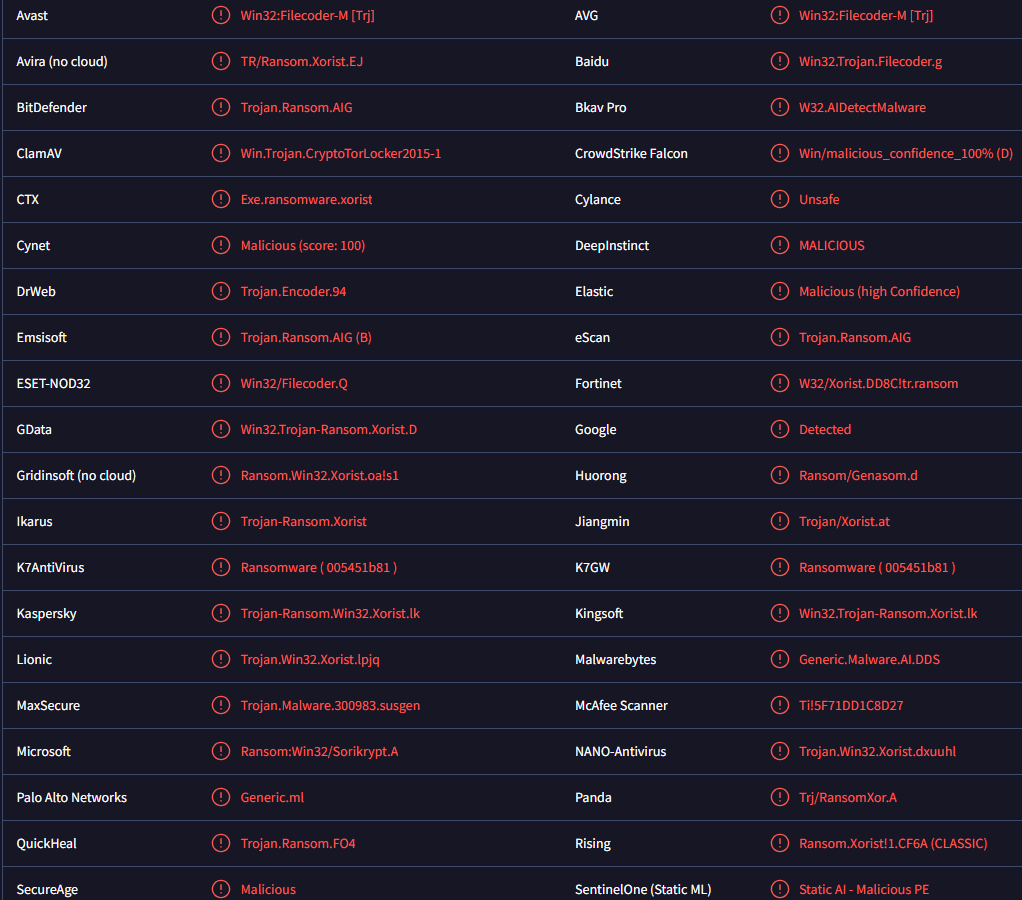
Shadaloo ransomware is also detected as:
- Win32:Filecoder-M [Trj] by Avast/AVG
- Trojan.Ransom.AIG by BitDefender
- Win32/Filecoder.Q by ESET
- Trojan-Ransom.Win32.Xorist.lk by Kaspersky
- Ransom:Win32/Sorikrypt.A by Microsoft
- Ransom.Win32.XORIST.SMA by TrendMicro
- Generic.Malware.AI.DDS by Malwarebytes
Offers
Download Removal Toolto scan for Shadaloo ransomwareUse our recommended removal tool to scan for Shadaloo ransomware. Trial version of provides detection of computer threats like Shadaloo ransomware and assists in its removal for FREE. You can delete detected registry entries, files and processes yourself or purchase a full version.
More information about SpyWarrior and Uninstall Instructions. Please review SpyWarrior EULA and Privacy Policy. SpyWarrior scanner is free. If it detects a malware, purchase its full version to remove it.

WiperSoft Review Details WiperSoft (www.wipersoft.com) is a security tool that provides real-time security from potential threats. Nowadays, many users tend to download free software from the Intern ...
Download|more


Is MacKeeper a virus? MacKeeper is not a virus, nor is it a scam. While there are various opinions about the program on the Internet, a lot of the people who so notoriously hate the program have neve ...
Download|more


While the creators of MalwareBytes anti-malware have not been in this business for long time, they make up for it with their enthusiastic approach. Statistic from such websites like CNET shows that th ...
Download|more
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.