Scp ransomware is a malicious infection that encrypts files. It comes from the Makop family of malware. The infection not only encrypts files but also steals them and threatens to release them publicly. It’s a very dangerous infection as files may be lost permanently.
Scp ransomware is a very dangerous malware that not only encrypts files but also steals them, threatening to publicly release the stolen data. Ransomware gangs have started doing this over the last couple of years as users and companies started backing up files and having efficient recovery plans in place, which makes traditional ransomware infections less effective. Stealing files in addition to encrypting them has proven to be effective as companies certainly do not want their files to be leaked.
Scp ransomware targets important files across various formats, including documents, text files, and images. When files are encrypted, they get an added extension .[unique ID].[studiocp25@hotmail.com].scp. For instance, a file named 1.txt would appear as 1.txt.[unique ID].[studiocp25@hotmail.com].scp after encryption. Unfortunately, these encrypted files cannot be opened unless they are put through a specific decryptor.
After the encryption process, a ransom note +README-WARNING+.txt. will be dropped. This note informs the victim that their files have been both encrypted and stolen, with a warning that the files will be publicly released unless the ransom is paid. A specific sum is not mentioned but it’s likely to be several thousand dollars.
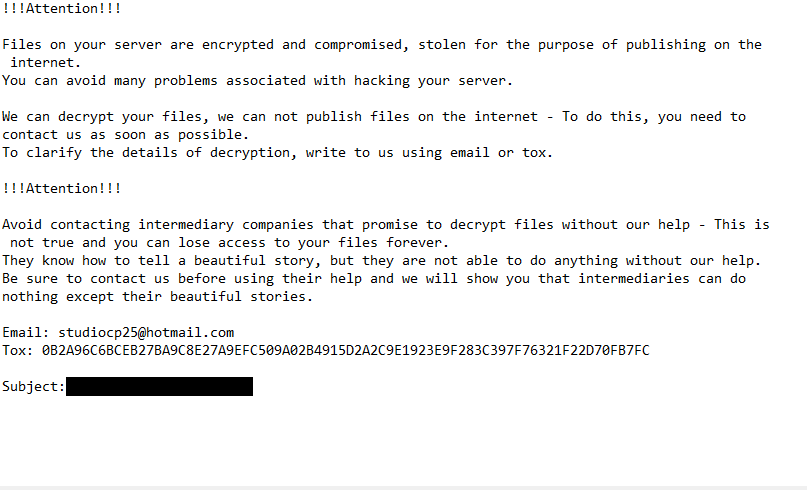
The full Scp ransomware +README-WARNING+.txt note is below:
!!!Attention!!!
Files on your server are encrypted and compromised, stolen for the purpose of publishing on the internet.
You can avoid many problems associated with hacking your server.We can decrypt your files, we can not publish files on the internet – To do this, you need to contact us as soon as possible.
To clarify the details of decryption, write to us using email or tox.!!!Attention!!!
Avoid contacting intermediary companies that promise to decrypt files without our help – This is not true and you can lose access to your files forever.
They know how to tell a beautiful story, but they are not able to do anything without our help.
Be sure to contact us before using their help and we will show you that intermediaries can do nothing except their beautiful stories.Email: studiocp25@hotmail.com
Tox: 0B2A96C6BCEB27BA9C8E27A9EFC509A02B4915D2A2C9E1923E9F283C397F76321F22D70FB7FCSubject: –
The general advice when it comes to ransomware is to not pay the ransom. It does not guarantee a decryptor or file recovery, as ransomware operators are cyber criminals, and there’s little to force them to keep their end of the deal. There are also no guarantees that they will not publicly release the stolen files.
For users with backups, file recovery should not be an issue. As long as they remove Scp ransomware before accessing the backup, they should be able to recover their files. Users who have no file recovery options are likely to have lost the files permanently.
How does ransomware enter computers?
Users who have poor browsing habits are at a significantly higher risk of infecting their computers with malware than those who have better habits. One effective way to prevent future malware infections is by improving your browsing habits. It’s also essential to familiarize yourself with common methods through which malware is distributed.
Being able to identify malicious emails is very important because it’s not uncommon to encounter emails carrying malware. Users whose email addresses have been leaked in the past are particularly likely to receive malicious emails.
Most users will be targeted with generic malicious emails which are relatively easy to identify. For example, such emails often have many grammar and spelling mistakes while the emails are impersonating official correspondence from certain companies.
Be wary of emails that greet you with generic words like “User,” “Member,” or “Customer,” as these could indicate spam or malicious emails. Legitimate companies address their customers by name in email correspondence to create a more personal feeling. Cybercriminals often resort to using generic words because they don’t have access to personal information besides an email address. If you receive an unsolicited email with a generic greeting and it includes an attachment, proceed with caution—the attachment might be malicious.
It’s also worth noting that emails with specific targets are considerably more sophisticated. They tend to have no grammar or spelling mistakes, include details that give credibility, and address the recipient by name. This is why it’s recommended to always scan unsolicited email attachments with anti-malware software or services like VirusTotal.
Malware is also commonly distributed through torrents. A lot of torrent sites are poorly monitored, which allows malicious actors to upload torrents with malware in them. Malware often lurks in torrents for entertainment content such as movies, TV shows, and video games. Downloading copyrighted materials via torrents not only is illegal but also compromises your computer’s security.
How to remove Scp ransomware
We do not recommend attempting to remove Scp ransomware manually, as it is a complex infection, and manual removal could result in more damage to the device. A good anti-malware program will remove Scp ransomware. Unfortunately, removing the infection will not restore encrypted files because a decryptor is necessary for that.
If you have a backup of your files, do not connect to it until you remove Scp ransomware from your device. Trying to access your backup while the ransomware is still present will result in your backed-up files becoming encrypted as well, leading to the permanent loss of those files.
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.