Defi ransomware is a ransomware infection that encrypts files. It comes from the Makop malware family. Encrypted files will have an extension that ends with .defi1328. Unfortunately, encrypted files will be unopenable unless you first use a decryptor on them. At the moment, only users who have backups can recover files for free.
Defi ransomware belongs to the Makop ransomware family. This version can be identified by the extension it adds to files it encryptes. The extension is as follows: .[unique ID].[wewillrestoreyou@cyberfear.com].defi1328. All victims will have unique IDs to help malicious actors differentiate between victims. For example, an encrypted 1.txt file would become 1.txt.[unique ID].[wewillrestoreyou@cyberfear.com].defi1328. Unfortunately, you will not be able to open any files that have this extension. This ransomware targets all personal files, including photos, videos, documents, etc.
Once the ransomware is done encrypting files, it will drop a +README-WARNING+.txt ransom note. The note contains information about what happened to users’ files and how they can be recovered. Unfortunately, the ransomware operators are demanding a ransom payment in exchange for a decryptor. The note does not mention the sum victims would need to pay but it’s likely to be around $1,000.
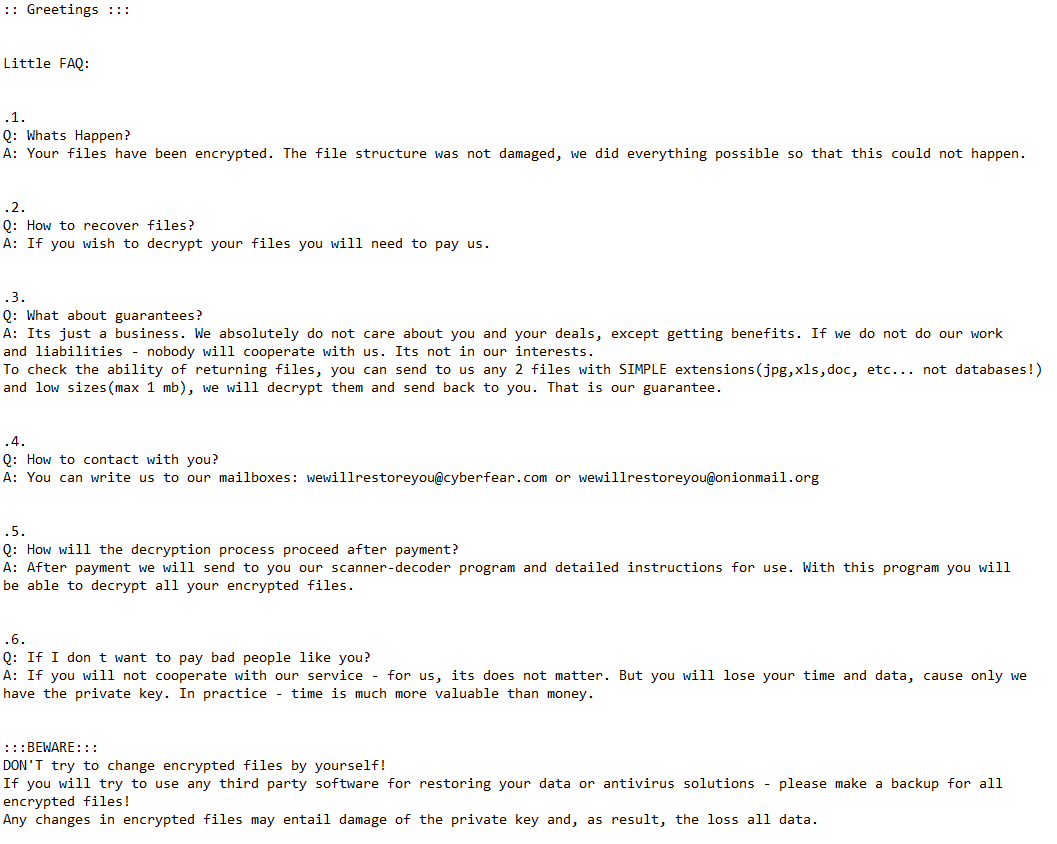
The full Defi ransomware ransom note is below:
::: Greetings :::
Little FAQ:
.1.
Q: Whats Happen?
A: Your files have been encrypted. The file structure was not damaged, we did everything possible so that this could not happen..2.
Q: How to recover files?
A: If you wish to decrypt your files you will need to pay us..3.
Q: What about guarantees?
A: Its just a business. We absolutely do not care about you and your deals, except getting benefits. If we do not do our work and liabilities – nobody will cooperate with us. Its not in our interests.
To check the ability of returning files, you can send to us any 2 files with SIMPLE extensions(jpg,xls,doc, etc… not databases!) and low sizes(max 1 mb), we will decrypt them and send back to you. That is our guarantee..4.
Q: How to contact with you?
A: You can write us to our mailboxes: wewillrestoreyou@cyberfear.com or wewillrestoreyou@onionmail.org.5.
Q: How will the decryption process proceed after payment?
A: After payment we will send to you our scanner-decoder program and detailed instructions for use. With this program you will be able to decrypt all your encrypted files..6.
Q: If I don t want to pay bad people like you?
A: If you will not cooperate with our service – for us, its does not matter. But you will lose your time and data, cause only we have the private key. In practice – time is much more valuable than money.
:::BEWARE:::
DON’T try to change encrypted files by yourself!
If you will try to use any third party software for restoring your data or antivirus solutions – please make a backup for all encrypted files!
Any changes in encrypted files may entail damage of the private key and, as result, the loss all data.
When it comes to ransomware, paying the ransom is never recommended for several reasons. The main reason is there are no guarantees that a decryptor will be sent if you pay. Keep in mind that you are dealing with cybercriminals, and they are unlikely to feel obligated to help you just because you pay. The money you pay would also go towards future criminal activities.
If you have a backup, you can start recovery as soon as you remove Defi ransomware from your computer. Make sure to use an anti-malware program to delete Defi ransomware because it’s a sophisticated infection.
How does ransomware enter computers?
It is important to mention that users with poor browsing habits are much more likely to infect their computers with malware compared to users with better habits. Therefore, it is strongly recommended to develop better online habits to avoid future malware infections. Becoming familiar with the most common malware infection methods is also important.
Being able to recognize malicious emails is crucial, especially if your email address has been leaked, as you are likely to receive a malicious email at some point in the future. Fortunately, unless you are specifically targeted, malicious emails are typically generic and easy to recognize due to grammar and spelling mistakes. The senders often pretend to be from legitimate companies, so the mistakes are very noticeable.
Beware of generic words like “User,” “Member,” “Customer,” etc. used to address you in emails, as they could be a sign of a malicious or spam email. Legitimate companies always address their users by their names to make the communication more personal. Malicious actors, on the other hand, are forced to use generic words because they often do not have access to personal information. If you receive an unsolicited email with a generic greeting and an attachment, be cautious as the attachment could be malicious.
It’s worth mentioning that malicious emails targeting specific users are more sophisticated. They are usually free of grammar and spelling mistakes, include credible information, and address recipients by name. To stay safe, it’s important to scan all unsolicited email attachments using anti-malware software or VirusTotal.
Torrents are another common method for distributing malware. Torrent sites are often poorly moderated, allowing malicious torrents to remain available for extended periods. Malware is frequently found in torrents for entertainment content such as movies, TV series, and video games. Downloading copyrighted material through torrents is not only illegal but also poses a risk to your computer’s security.
How to remove Defi ransomware
Do not try to remove Defi ransomware manually because you could cause your computer additional damage. It’s a complex infection that requires a professional program to get rid of. Otherwise, you’re risking more damage.
If you have a backup, do not connect to it until you fully delete Defi ransomware from your device. If no backup is available, back up the encrypted files and occasionally check NoMoreRansom for a free Defi ransomware decryptor.
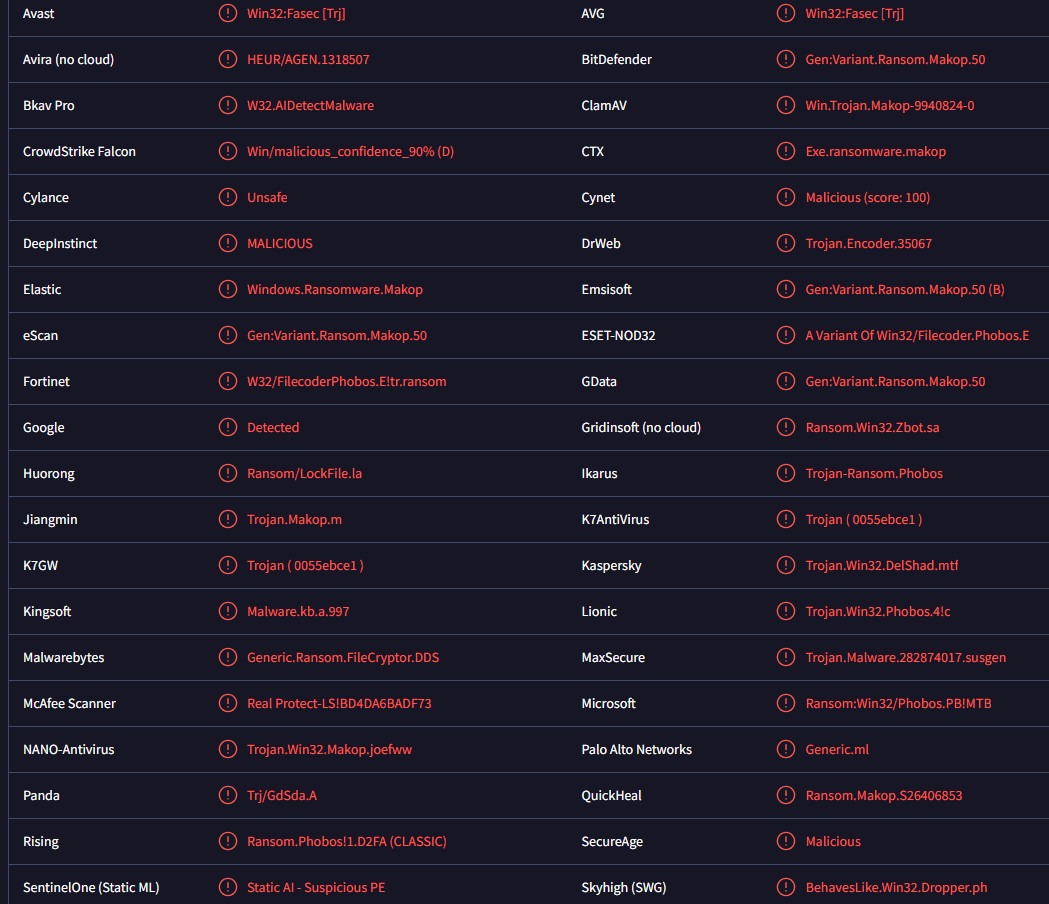
Defi ransomware is detected as:
- Win32:Fasec [Trj] by Avast/AVG
- Generic.Ransom.FileCryptor.DDS by Malwarebytes
- A Variant Of Win32/Filecoder.Phobos.E by ESET
- Trojan.Win32.DelShad.mtf by Kaspersky
- Ransom:Win32/Phobos.PB!MTB by Microsoft
- Ransom.Win32.MAKOP.SMYXCBKT by TrendMicro
Offers
Download Removal Toolto scan for Defi ransomwareUse our recommended removal tool to scan for Defi ransomware. Trial version of provides detection of computer threats like Defi ransomware and assists in its removal for FREE. You can delete detected registry entries, files and processes yourself or purchase a full version.
More information about SpyWarrior and Uninstall Instructions. Please review SpyWarrior EULA and Privacy Policy. SpyWarrior scanner is free. If it detects a malware, purchase its full version to remove it.

WiperSoft Review Details WiperSoft (www.wipersoft.com) is a security tool that provides real-time security from potential threats. Nowadays, many users tend to download free software from the Intern ...
Download|more


Is MacKeeper a virus? MacKeeper is not a virus, nor is it a scam. While there are various opinions about the program on the Internet, a lot of the people who so notoriously hate the program have neve ...
Download|more


While the creators of MalwareBytes anti-malware have not been in this business for long time, they make up for it with their enthusiastic approach. Statistic from such websites like CNET shows that th ...
Download|more
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.