DavidHasselhoff ransomware is file-encrypting malware that belongs to the MedusaLocker ransomware family. It’s considered to be a dangerous infection because not only does it encrypt files, but it also claims to have stolen them as well. If users do not agree to pay, their files will supposedly be released publicly.
DavidHasselhoff ransomware is a very dangerous malware infection because it not only encrypts files but also steals them and threatens to release them. DavidHasselhoff ransomware targets all important files, including documents, text files, images, etc. All encrypted files will have a .247_davidhasselhoff extension added to them. For example, 1.txt file would become 1.txt.247_davidhasselhoff if encrypted. Unfortunately, none of the encrypted files will be openable unless they’re put through a decryptor.
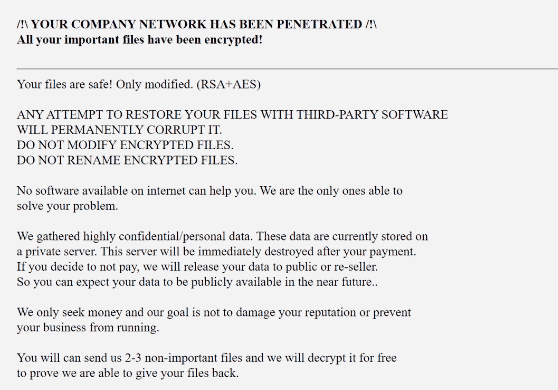
Once files have been encrypted, the ransom will drop a How_to_back_files.html ransom note. The note explains that files have been encrypted and stolen, and will be published publicly unless you agree to pay a ransom.
The full DavidHasselhoff ransomware note is below:
YOUR PERSONAL ID:
–/!\ YOUR COMPANY NETWORK HAS BEEN PENETRATED /!\
All your important files have been encrypted!Your files are safe! Only modified. (RSA+AES)
ANY ATTEMPT TO RESTORE YOUR FILES WITH THIRD-PARTY SOFTWARE
WILL PERMANENTLY CORRUPT IT.
DO NOT MODIFY ENCRYPTED FILES.
DO NOT RENAME ENCRYPTED FILES.No software available on internet can help you. We are the only ones able to
solve your problem.We gathered highly confidential/personal data. These data are currently stored on
a private server. This server will be immediately destroyed after your payment.
If you decide to not pay, we will release your data to public or re-seller.
So you can expect your data to be publicly available in the near future..We only seek money and our goal is not to damage your reputation or prevent
your business from running.You will can send us 2-3 non-important files and we will decrypt it for free
to prove we are able to give your files back.Contact us for price and get decryption software.
email:
wehavesolution@onionmail.org
solution247days@outlook.com* To contact us, create a new free email account on the site: protonmail.com
IF YOU DON’T CONTACT US WITHIN 72 HOURS, PRICE WILL BE HIGHER.
Paying the ransom is never recommended when it comes to ransomware because it does not guarantee that malicious actors will keep their end of the deal considering there is nothing to force them to.
If you have a backup, you can start recovering your files as soon as you remove DavidHasselhoff ransomware from your computer. Make sure to use a good anti-malware program because it’s a very complex infection. Once the ransomware is gone, it’s safe to connect to your backup.
If you do not have a backup, there currently is no free DavidHasselhoff ransomware decryptor.
How does ransomware enter computers?
We should note that users with poor browsing habits are much more likely to infect their computers with malware compared to users with better habits. One of the best ways to avoid future malware infections is to develop better browsing habits. It’s also important to become familiar with the most common malware infection methods.
Knowing what to look for in emails to recognize them as malicious is very important. Particularly if your email address has been leaked, as you will likely receive a malicious email at some point in the future. Fortunately, malicious emails are typically generic and easy to recognize due to grammar and spelling mistakes. Because senders often pretend to be from legitimate companies, the mistakes are very noticeable. Sophisticated malicious emails are usually reserved for specific targets whose personal information malicious actors have.
Be cautious of emails that address you with generic words like “User,” “Member,” or “Customer,” as they could be signs of malicious or spam emails. Legitimate companies will always use your name to address you in emails if you are their customer. Malicious actors, however, often resort to generic greetings because they lack access to personal information. If you receive an unsolicited email with a generic greeting and an attachment, be cautious, as the attachment could be malicious.
It’s important to note that malicious emails targeting specific users will appear much more sophisticated. They usually have no grammar or spelling mistakes, contain information to give the email credibility, and address recipients by name. To stay safe, make sure to scan all unsolicited email attachments using anti-malware software or VirusTotal.
Torrents are a common way malware is distributed. Torrent sites are often not well-moderated, which means that malicious torrents can remain up for a long time. Malware is often found in torrents for entertainment content like movies, TV series, and video games. Downloading copyrighted material through torrents is not only illegal but also poses a risk to your computer’s security.
How to remove DavidHasselhoff ransomware
We don’t recommend trying to remove DavidHasselhoff ransomware manually because ransomware is a complex infection, and unless you know exactly what to do, you could cause your computer additional damage. If you use a reliable anti-malware program, it should have no issues with DavidHasselhoff ransomware removal.
If you have a backup of your files, do not connect to it until you fully delete DavidHasselhoff ransomware from your device. If the ransomware is still on your device when you connect to your backup, your backed-up files could become encrypted as well. If that were to happen, the files would be lost permanently. If you don’t have a backup, back up the encrypted files and check NoMoreRansom for a free DavidHasselhoff ransomware decryptor.
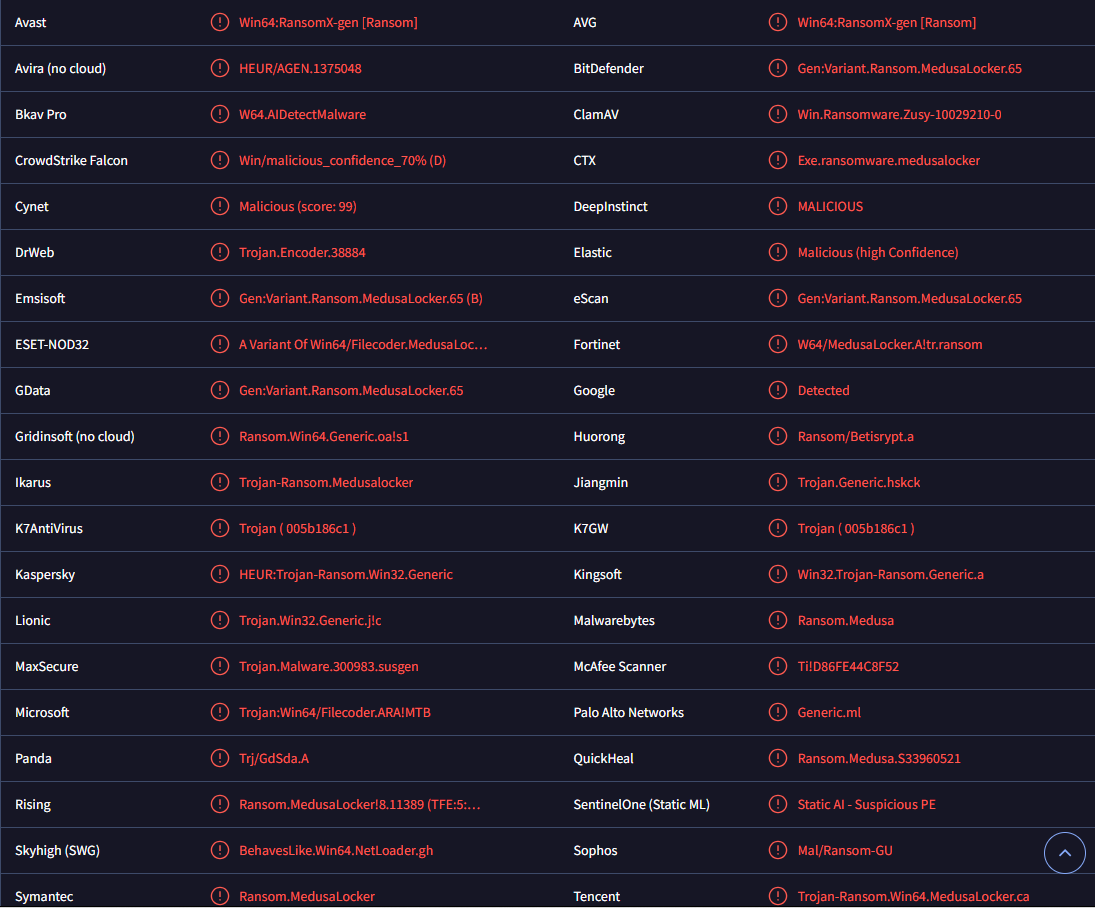
DavidHasselhoff ransomware is detected as:
- Win64:RansomX-gen [Ransom] by Avast/AVG
- A Variant Of Win64/Filecoder.MedusaLocker.A by ESET
- HEUR:Trojan-Ransom.Win32.Generic by Kaspersky
- Trojan:Win64/Filecoder.ARA!MTBby Microsoft
- Gen:Variant.Ransom.MedusaLocker.65 by BitDefender
- Ransom.Medusa by Malwarebytes
Site Disclaimer
2-remove-virus.com is not sponsored, owned, affiliated, or linked to malware developers or distributors that are referenced in this article. The article does not promote or endorse any type of malware. We aim at providing useful information that will help computer users to detect and eliminate the unwanted malicious programs from their computers. This can be done manually by following the instructions presented in the article or automatically by implementing the suggested anti-malware tools.
The article is only meant to be used for educational purposes. If you follow the instructions given in the article, you agree to be contracted by the disclaimer. We do not guarantee that the artcile will present you with a solution that removes the malign threats completely. Malware changes constantly, which is why, in some cases, it may be difficult to clean the computer fully by using only the manual removal instructions.