Malicious applications created specifically for Android phones have been spreading for a while now. Some of them can lock the device and present the user with a fake notification claiming to have come from a government facility. Others manage to not only restrict access to the phone, but also to encrypt the files that are stored on it. A new threat to Android devices that can silently obtain Device Administrator rights and lock out users by changing their lock-screen PIN will be discussed in this article.
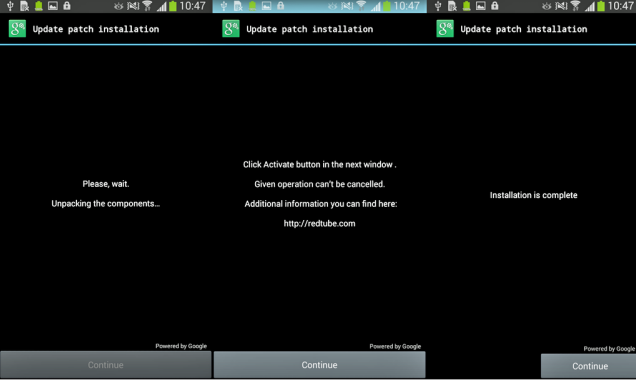
The ransomware application, often referred to as Android/Lockerpin.A, spreads by using social engineering tricks. It is disguised as an application for viewing pornographic videos called Porn Droid. The application cannot be downloaded from Google Play Store, which means that the only way to acquire it is via third party sources. The malicious app mostly infects devices located in the USA, however, other countries may be affected as well.
Once the malware gets installed, it obtains Device Administrator privileges by overlaying the activation window with a fake “Update patch installation” window. If the user agrees to this installation, the threat obtains Administrator rights silently. Not long after that, a fake alert that supposedly comes from the FBI claims that the user has to pay $500 for viewing forbidden pornographic content. After the bogus notification is displayed, the malware locks the screen and resets the lock-screen PIN. The user can no longer access the device without having root privileges or factory resetting it, which will result in the loss of all data stored on the Android.
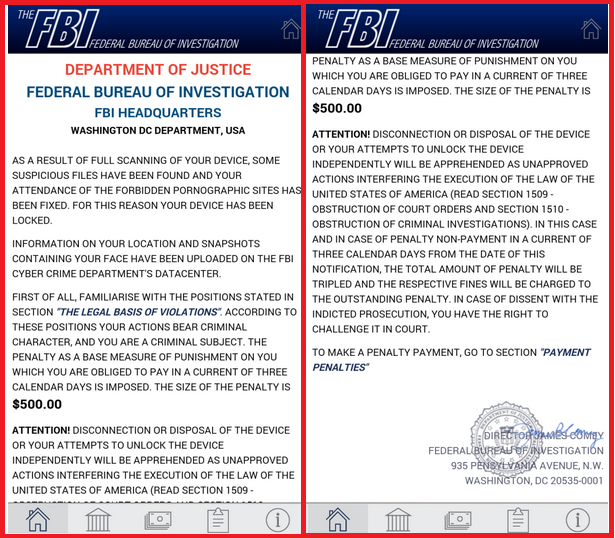
Another aspect of this infection that should be mentioned is its use of aggressive self-defense tactics that have never been used in previous Android malware. If the user attempts to deactivate Device Administrator rights for the ransomware, it will reactivate the privileges by using the already registered call-back function or by showing a bogus window, which claims that the operation is forbidden. In addition to this, the malicious application can even attempt to kill anti-virus processes in order to prevent the user from uninstalling it.
Unlocking the device without a factory reset is only possible if it is rooted or if it has an MDM solution that can restore the PIN. If the device is rooted, the user can connect to it by Android Debug Bridge and delete the file in which the PIN is stored. However, USB Debugging must be enabled beforehand for this to succeed. The following set of commands can be used in order to unlock the phone:
- >db shell
- >su
- >rm /data/system/password.key
Once the user runs these commands, the password lock screen is removed and it is possible to access the device.
In conclusion, we would like to advise that you be especially careful with software that you download onto your Android as well as your other devices. Do not use third party sources unless you are sure that they can be trusted. Malicious programs are getting more and more sophisticated, which means that it is extremely important to have powerful anti-malware tools capable of protecting you even from the newest and most dangerous threats.