Cyber crime comes in a variety of forms, one of the most common being ransomware, a type of malware infection that encrypts files and demands money in return for decrypting them. Ransomware, in the last five or so years, has become a significant nuisance to everyone, including individual users, companies and organizations, goverment agencies and even healthcare institutions. 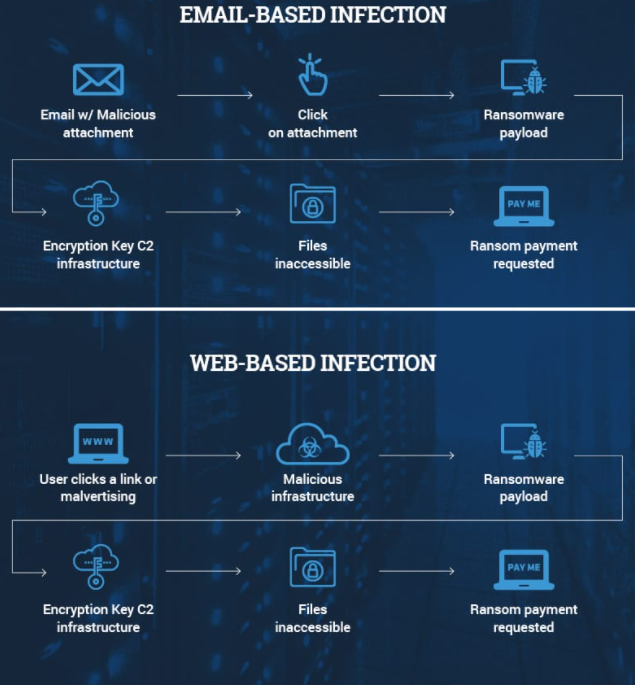
The estimated cost of ransomware attacks has exceeded $20 billion in just 2020 alone, more than double the amount of that in 2018. The cost of damages is only going to increase over the coming years, with more and more companies and organizations falling victim. And with ransomware-as-a-service (Raas) becoming widely available to anyone who wishes to turn to this particular type of cyber crime, ransomware became an even bigger threat. Cyber criminals can now just rent out ransomware and buy access to systems to launch the ransomware on, while putting in minimal effort and requiring little skill.
While regular users are still at risk of becoming victims of ransomware attacks, it’s businesses and organizations that have the biggest risk. Regular users are usually victims of very generic, often easily avoidable ransomware attacks, but organizations are targeted by very specific and sophisticated ransomware strains. The stakes are also much higher for the latter, as ransomware demands often exceed millions of dollars.
Businesses and organizations also face another problem, ransomware gangs now not only encrypt files and cause significant disruption to everyday operations but also steal data and threaten to release it publicly if a ransom is not paid. Many ransomware have made good of that promise and have indeed publicly released potentially sensitive data stolen from companies who made the decision to not pay.
For individual users, avoiding ransomware means developing better browsing habits and not engaging in illegal activities on the Internet. For businesses and organizations, however, it’s much more complicated.
Below you can find the methods ransomware most commonly uses to infect systems, applicable to both individual users and bigger targets.
Pirating copyrighted content
It’s no secret that you can get just about any kind of paid movie, TV series, game, software, etc., for free by pirating. Whether you should do it or not is another question, but the fact is that it’s possible. And because many people choose this option to get their favorite content, it’s creates the perfect opportunity for malicious actors to distribute malware. Not to mention the fact that sources that have pirated content are often very poorly regulated, which allows cyber crooks to easily distribute their malware.
In most cases, users pick up ransomware via torrents for entertainment content and when downloading software cracks. You cannot trust sites like the Pirate Bay or software crack forums to provide you with safe content when the whole point of those platforms is to give access to stolen content. The majority of torrent sites in particular are notoriously badly regulated, which allows malicious parties to easily upload their malicious content onto the platforms.
Torrents for popular content more often than not have concealed malware in them. For example, when popular TV series Game of Thrones was airing, torrents for episodes were often malware. The same can be said about any highly anticipated/popular movie, TV series, and video game.
In addition to torrents containing malware, torrent sites themselves can often be classified as malicious. The sites display various scams, including fake virus alerts, prompts to download potentially dangerous programs, and “you have won a prize” scams. Furthermore, many torrent websites may be more vulnerable to exploitation by malicious parties, which could allow them to initiate drive-by downloads.
The easiest way to avoid picking up ransomware and other kinds of malware infections from pirating websites is to not torrent. However, if you are not concerned with that fact that you are essentially stealing content, at the very least have anti-virus software installed for when you inevitably end up downloading malware.
Email attachments
Malspam and their attachments are one of the most common ways malware, ransomware especially, is distributed. This applies to both regular users and corporate networks. Various social engineering tactics are used to trick users into opening email attachments, doing which would initiate the malware. The malicious attachments come in various formats, including Word, Excel, PDF and ZIP.
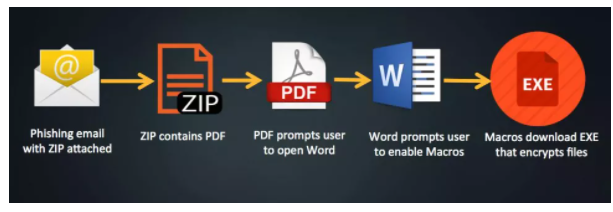
Malspam campaigns range from very basic ones to quite sophisticated, the latter of which usually have specific targets, such as companies or government institutions. The generic malspam campaigns are very easily recognizable, as long as users don’t rush to open unsolicited email attachments. However, the sophisticated ones can be extremely difficult to detect, judging from the numerous companies and institutions that have fallen victim.
How to avoid getting infected:
- inspect the sender’s email address;
The sender’s email address should be the first thing you check when you receive an unsolicited email with an attachment because it’s often a big giveaway. Unless they have specific targets, ransomware emails are often sent from very generic email addresses made up of random combinations of numbers and letters. However, even if the email address looks legitimate, always check whether it actually belongs to whomever the sender claims to be.
- look for grammar and spelling mistakes in unsolicited emails;
Whether it’s intentional or not, malspam, phishing and other malicious emails often contain very obvious grammar and spelling mistakes. If you receive an email (especially if it’s the generic automatic one) from a company whose services you use, the email will not have grammar/spelling errors as they are seen as unprofessional. If, for example, you receive an email with mistakes from someone claiming to be your bank, consider that a big red flag.
- take note of how the email addresses you;
You likely have noticed that when a company whose service you use sends you an email, it addresses you by name. For example, if you use the streaming service Netflix, they would address you by the name of the main Netflix user profile. If you have a bank account with for example, Barclays, official correspondence will address you by your last name. Never will generic words like “User”, “Member”, “Customer”, etc., ever be used to address you in legitimate emails by services you use. If an email that uses generic words to address you asks you to open an attachment because it’s an important document, you should be very careful.
- scan email attachments with anti-virus software or VirusTotal;
It’s highly recommended to scan all email attachments with anti-virus software or VirusTotal before opening them. You can upload the email attachment onto VirusTotal, and it would show you whether any of the tens of anti-virus programs detect the file as malicious.
- do not click on unfamiliar links.
In some cases, emails contain links instead of email attachments. Clicking on a malicious link would take you to a website where malware like ransomware may be hiding.
Malicious advertising
Malicious advertising, or malvertising in short, is also a tactic used by ransomware distributors to spread their malicious software. The way malvertising works is malicious actors insert malicious code into advertisements and then use legitimate advertising networks to display those ads to users. If users interact with the malicious ad, they will be redirected to a malicious server that hosts an exploit kit, which can then execute. Exploit kits are malware that check the infected device for vulnerabilities to exploit. By exploiting a vulnerability, the exploit kit can essentially allow ransomware to enter a computer.
Malicious ads can be found on completely legitimate websites, though they are usually quickly discovered and removed. Unfortunately, this means that interacting with ads even on legitimate sites is not always safe.
How to avoid getting infected:
- regularly install updates;
To prevent malware from taking advantage of vulnerabilities, make sure to install updates on a regular basis. Whenever developers become aware of a vulnerability that could be exploited, they release an update to patch it. All you need to do is install it. You can turn on automatic updates in many cases, and we highly recommend doing that.
- have anti-virus software and adblocker installed;
Having anti-virus software installed is a must in order to prevent malware infections, including ones that spread via malicious advertising. A reliable anti-virus program will prevent infections like ransomware from getting in or doing any damage. Installing an adblocker extension is also a good idea, as it would block ads and prevent pop-ups.
- avoid interacting with ads on high-risk websites.
When browsing high-risk websites, it’s a good idea to not click on any advertisements, as there is a high chance they will be unsafe. Websites that have pirated content, free streaming pages and pornography sites are among the most high-risk, so extra caution should be taken when visiting them. Having adblocker installed at the very least is recommended.
Drive-by downloads
Similarly to malvertising, drive-by downloads involve malicious actors injecting malicious code into websites and then using exploit kits to infect computers. Legitimate websites can sometimes be compromised and result in drive-by downloads but it’s not particularly common, as it involves essentially hacking the sites and it’s not always that easy when there’s sufficient protection measures taken.
These downloads can occur without users noticing anything amiss, it’s usually enough to just visit the site for the download to start. This could lead to all kinds of infections, including ransomware.
How to avoid getting infected:
- have anti-virus software installed.
Having anti-virus software installed is a must in order to prevent malware infections, including ones that spread via malicious advertising. A reliable anti-virus program will prevent infections like ransomware from getting in or doing any damage.
Remote Desktop Protocol (RDP)
Remote Desktop Protocol, or RDP in short, is a tool that allows users to connect to another computer or server using a network connection. Unsurprisingly, cyber criminals saw an opportunity to distribute ransomware via RDP. It’s currently one of the most widely used infiltration methods by ransomware, especially when it comes to infecting organizations rather than individual users. The notorious Dharma and GandCrab ransomware families are known to exploit Remote Desktop Protocol to infect computers.
The biggest danger is leaving a RDP port open to the Internet as it essentially allows anyone to connect to the remote server. If an attacker is able to successfully connect to it, he/she would have access to the server and could perform a variety of actions, such as installing ransomware. Cyber criminals are able to scan the Internet for open RDP ports, to which they then attempt to log in by either guessing the credentials or using stolen ones. Once the attacker is in the system, he/she would proceed to disable security systems to make the network vulnerable, and then deliver the payload aka install ransomware.
How to avoid getting infected:
- use a VPN;
It’s highly recommended to use a VPN in order to make accessing remote networks safe.
- have strong passwords and enable multi-factor authentication;
The majority of successful RDP attacks occur because of weak login credentials. Creating a long, random and most importantly, unique password would prevent attackers from being able to successfully carry out attacks via RDP. However, because it’s always possible to compromise passwords, it’s recommended to enable multi-factor authentication to make it more difficult for unauthorized parties to log in.
- use a firewall to limit who has access.
You can use a firewall to limit which IP addresses or what range of IP addresses have access to RDP.