What is FluBot Malware (Android)
FluBot Malware (Android) is a very dangerous malware infection that affects Android devices. It has recently started spreading at an alarming rate, with thousands of people, particularly in Australia and Europe, reporting to authorities that they have become victims. The malware is distributed via text messages with links that lead to the download, and once installed, the malware requests various permissions and attempts to steal both personal and financial information. As far as distribution goes, it’s pretty typical and low-effort but the actual malware is quite sophisticated.
The malware, while first noticed to be spreading via SMS messages in early August, has recently made the news due to how widespread it has become in Australia and Europe. According to the media, thousands of Australians have recently received these malicious messages, with one person reportedly losing $4000.
The malware is pretty stealthy which makes it difficult for users to notice it installed on their devices. However, if you recall receiving a suspicious SMS claiming that you have a new voice message, clicked on the link, and installed the “app”, you need to act immediately. The first course of action is to secure all your accounts using a malware-free device. You also need to remove FluBot Malware (Android) as soon as possible, either using an anti-virus app or by taking the infected device to a professional.
FluBot Malware (Android) distribution methods
The malware seems to be spreading quite quickly, or at least it’s trying to. It’s mainly distributed via text messages that claim users have a new voicemail. Users have reported that they have received numerous messages on the same day, all from different numbers. The text message contains a link to the supposed voice message, which if clicked would direct users to an app called Voicemail71.APK. Downloading the app would infect the device with malware. There are also other “apps” that users are asked to download instead of Voicemail71.APK.
The messages distributing FluBot Malware all have very obvious grammar mistakes, which indicates that they are deliberate. Cybercriminals often use this technique to weed out users who may be less likely to fall for whatever the scam does next. Even if more suspicious users end up downloading this malicious app, they may quickly realize what’s going on and promptly get rid of it, not allowing malicious actors to steal anything.
For future reference, you should never click on links in text messages, even if they appear to come from safe phone numbers. Malicious actors use various techniques to make their messages appear like they’re coming from legitimate senders, which is why you should always be very careful. Keep in mind that your bank, government agency, delivery service, etc., will never send text messages that contain links, as that is considered to be an unsafe practice due to the misuse by malicious actors.
What does the malware do?
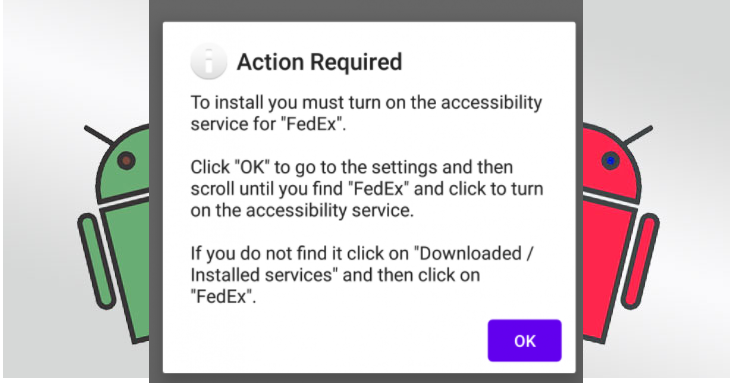
While the distribution method is rather basic and low-effort, the actual scam is rather sophisticated. When users click on the link and the download is complete, the installation process will request various permissions for the app, including write/read/send SMS messages, read contacts, start phone calls, keep the device awake, etc. The FluBot malware receives commands from a Command and Control (C&C) server and can be commanded to open URLs, upload SMS messages, uninstall apps, extract the contact list, and even disable Google Play Protect. And considering that it’s primarily a banking trojan, it can also display fake windows asking to provide banking information and credit card details.
Considering the trojan’s capabilities and stealth, it can be difficult to notice once it’s already installed. And while you go about your regular smartphone use, the malware would be stealing your login credentials, personal as well as banking information. The way it does that is by displaying fake login and other similar pages. For example, when you’re trying to log in to your online bank account, the malware could display a fake login window, and if you type in your login credentials and codes, they would be sent to the malicious actors behind this scam. The same applies to other personal information.
If malicious actors are successful in stealing personal and financial information, they can do a lot of damage. Cybercriminals could steal victim’s identities and their money.
FluBot Malware (Android) removal
Considering that it’s a very serious malware infection, you need to remove FluBot Malware (Android) immediately. If you recall clicking on a questionable text message that led to you downloading some app, you need to install a security app to scan your device. If you do not feel confident you can delete FluBot Malware (Android) yourself, take your device to professionals who will do it for you.
It should also be said that removing the malware is not the only thing you need to do. Since the malware is capable of recording passwords, assume that every password you have entered since the malware infection has been stolen. You need to change all your passwords immediately but make sure to do it on a clean device. If you have accessed your online bank account or typed in your payment card details, you need to contact your bank and monitor all your transactions for anything suspicious.