During a bug bounty related investigation Jouko Pynnönen, a security researcher from Finland, has discovered several vulnerabilities in the Formidable Forms, which could possibly expose websites to attacks.
 Formidable Forms is a WordPress plug-in used to create contact forms, polls, surveys and various kinds of other forms for websites. It has two versions available, a free and a paid one (Formidable Forms Pro), and more than 200,000 active installs.
Formidable Forms is a WordPress plug-in used to create contact forms, polls, surveys and various kinds of other forms for websites. It has two versions available, a free and a paid one (Formidable Forms Pro), and more than 200,000 active installs.
Below the example shared by the expert:
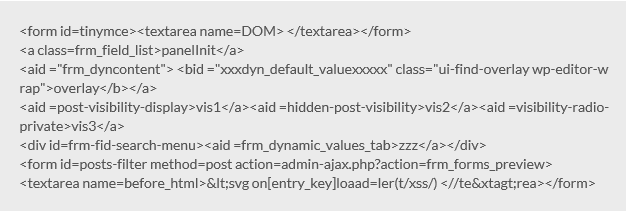
The researcher names an exploitable SQL injection as the most severe issue as it can be used to access website contest, such as user credentials and data submitted via Formidable Forms. He also notes that another vulnerability could expose data submitted through forms created with the Formidable Forms plug-in. Both of these flaws are related to how Formidable Forms implements shortcodes, which is a WordPress-specific code that basically permits users to add content to their sites with little effort.
According to the researcher:
“The plugin implemented a form preview AJAX function accessible to anyone without authentication. The function accepted some parameters affecting the way it generates the form preview HTML. Parameters after_html and before_html could be used to add custom HTML after and before the form. Most of the vulnerabilities relied on this feature.”
Pynnönen also discovered vulnerabilities that could be exploited in reflected and stored cross-site scripting (XSS). Attackers could exploit the stored XSS to execute arbitrary JavaScript code in the context of an administrator’s browsing session. The attacker could inject a malicious code through the forms, which would get executed when the admin views it in the WordPress dashboard.
“Administrators can view data entered by users in Formidable forms in the WordPress Dashboard. Any HTML entered in forms is filtered with the wp_kses() function. This isn’t enough to prevent dangerous HTML as it allows the “id” and “class” HTML attributes and e.g. the <form> HTML tag. It was possible to craft HTML code which would result in attacker-supplied JavaScript to be executed when the form entry is viewed,” Pynnönen explains.
In the same bug bounty investigation, Pynnönen also noticed that if the iThemes Sync WordPress maintenance plugin is present alongside Formidable Forms, the attacker could exploit the SQL injection vulnerability to access user ID and authentication key.
“This information can be used to control the WordPress system via the iThemes Sync functions. They include e.g. functions to add new administrator users or install and activate WordPress plugins,” the researcher explains.
Pynnönen was invited to participate in a bug bounty program run by a company in Singapore. The vulnerabilities were reported, and Pynnönen was rewarded $4,500 for the SQL injection flaw, and smaller amounts for other vulnerabilities.
Formidable Forms have patched the vulnerabilities in the versions 2.05.02 and 2.05.03, while iThemes Sync does not view the attack vector as a vulnerability so a patch was not released.