Over the years, Facebook has become a source of information about everything. There are news articles, music sharing, everything you could possible want in one place, so of course people with questionable intentions are using that as well. You must encounter all kind of spam, some more obvious than others, fake news, etc. But we all have those ‘safe’ websites that we would not hesitate to click on if the content seemed interesting.
And in July 2017 , Facebook eliminated the option that allowed posters to edit the tittle, description, image, etc., which makes it safer to click on links since you know exactly where you will be led to. Right? While it would nice if that were the case, security specialists Barak Tawily has demonstrated that it is possible for posters with malicious intent to spoof URLs, making them appear legitimate while redirecting you to malicious sites. And Facebook’s method of fetching link previews allows this to happen.
Spammers exploit the method Facebook uses to fetch link previews
When someone shares a link, video, etc., Facebook scans for Open Graph meta tags, specifically the “og:url,” “og:image” and “og:title” tags. This basically is the URL, image and the title of the shared link. What Facebook does not do is, it does not check whether the link in “og:url” matches the page URL. So as long as you add a legitimate URL in “og:url”, you can lead users to all kinds of websites.
“In my opinion, all Facebook users think that preview data shown by Facebook is reliable, and will click the links they are interested in, which makes them easily targeted by attackers that abuse this feature in order to perform several types of attacks as I mentioned above (phishing campaigns/ads/click fraudpay-per-click),” Tawily explains in his blog post.
Facebook will not fix the flaw
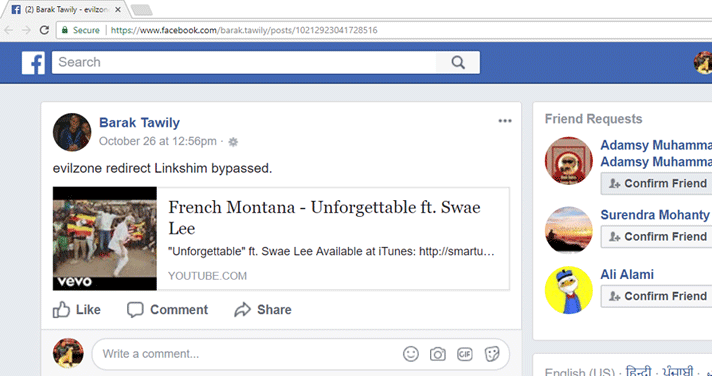
The security researcher forwarded what he found to Facebook, but the social media company did not recognize it as a security issue. Facebook also mentioned that it uses “Linkshim” in order to avoid such attacks. What the “Linkshim” system does is, it scans the URLs for blacklisted links. It also scans the site for malicious content, expanding the blacklisted site list constantly. However, Tawily was able to by pass this as well.
“I tried to publish a link that redirects user’s browser to “evilzone” but it was detected and removed, then I thought, what if I supply Facebook bot just a normal fake HTML without any malicious code, but supply victims the malicious HTML?”
While there is little you can do to protect yourself from this kind of attack, there are still some precautions that you can take. You can always hover over the link without actually clicking on it, if it matches the displayed URL, you can safely click on it. Look out for weird, grammatically incorrect sentences, and if someone you do not use English to communicate with sends you a message in strange English with a link, first inquire about it, and only then click on it. If you are very skeptical about clicking on a link, you can always search for the article/video manually. In short, remain vigilant, even when the link appears to be trustworthy.