What is Escobar Malware (Android)?
Last year’s newcomer Aberebot Android malware has been rebranded into “Escobar”, the same old banking trojan but with new features. Judging from the author’s posts on hacker forums, this Android malware is still in the testing phase but it will likely start affecting users in the near future. The updated malware comes with quite alarming features, such as the ability to steal one-time codes from Google Authenticator, an app used by many users to add an extra layer of security to their accounts.
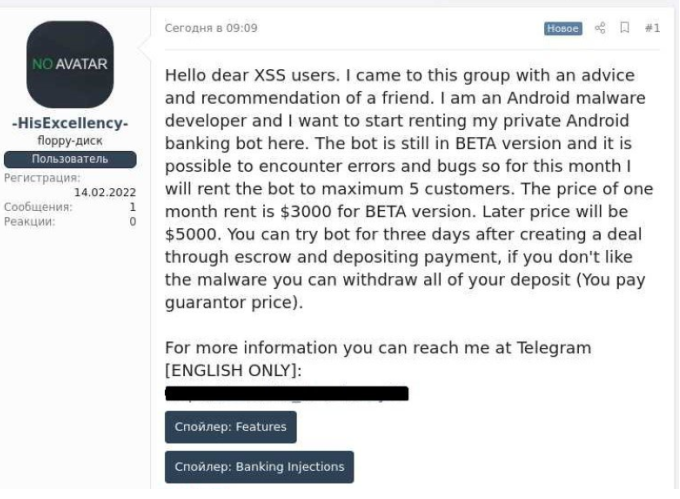
Escobar malware’s initial version first appeared mid-2021 and in February 2022, a post on a Russian-speaking forum appeared inviting cybercriminals to use a BETA version of Escobar. The author is offering Escobar malware as malware-as-a-service (MaaS) which essentially allows cybercriminals who have very little skill to carry out malicious attacks. According to the author’s post, the BETA version costs $3000/month but once the full version is released, the price will go up to $5000/month.
Escobar Malware is a banking trojan so its primary target is users’ banking information. When it’s initiated, the malware requests 25 permissions in total. Among its capabilities are: audio recording, reading SMS, reading/writing storage, making calls, tracking location, uninstalling apps, injecting URLs into web browsers, and using the phone’s camera. But most importantly, the malware essentially allows attackers to completely take over the phone. Granting all these permissions to the malware essentially means that it can do anything, including showing fake login pages to phish login credentials, as well stealing multi-factor authentication codes from SMS and/or apps like Google Authenticator.
Escobar Malware is yet to be fully released so it’s currently unclear how exactly it will be distributed. However, considering that the malware author is planning on renting it out, we can expect that there will be many distribution methods. There are reports, however, about the malware being disguised as a McAfee anti-virus app. The way this works is users may come across fake alerts about viruses on their Android device when browsing certain websites. These alerts use various scare tactics to intimidate users into downloading the offered apps. And users would give these apps all kinds of permissions because they know the names like McAfee and trust the apps. This just goes to show how important it is that users only download apps from legitimate sources like the Google Play Store. Google’s Play Store is strictly regulated, and while some malicious apps are able to bypass the security measures, it’s still much safer to download apps from it instead of unknown third-party app stores.
While Escobar Malware (Android) will likely be a dangerous malware infection, it doesn’t appear to be anything groundbreaking. So the usual methods for avoiding malware apply. And for Android devices that are already infected, it’s best to use an anti-virus app to remove Escobar Malware (Android).
Ways you can protect your Android device from Escobar Malware and prevent credential theft
There are certain actions you can take to protect your Android device from Escobar Malware, as well as many other threats that can affect Androids.
- Only use legitimate app stores to download apps.
As we’ve already said, legitimate app stores like Google’s Play Store have very strict security measures. So the chances of encountering malicious apps on Google Play are much lower than that of third-party app stores. However, it’s also important to keep in mind that those security measures are not absolute, and some malicious apps are able to bypass them. It has happened in the past, which is why it’s important that you always double-check everything before installing an app. Check the developer, reviews, permission requests, etc.
- Consider using an anti-virus app.
It may be a good idea to have an anti-virus app installed on your Android device. If you accidentally install a malicious app, it would be immediately detected by the anti-virus installed on your device, before it could do any damage. However, if you do plan to use an anti-virus Android app, make sure to download it from a legitimate source.
- Always review app permissions.
When installing any app, you are asked to give it certain permissions so that the app can work as intended. For example, a photo editor app would request access to your photos/camera. The permissions an app requests can tell a lot about what the app does. So when installing any app, whether it’s from Google Play Store or from anywhere else, always review permissions. If you’re installing a flashlight app but it requests access to your SMS or data, carefully consider why a basic utility app would need such permissions.
- Use a password manager that can differentiate between fake and legitimate login screens.
Password managers are very convenient tools that not only generate/store passwords but can also help identify phishing sites. Password managers can automatically fill in saved login credentials on websites’ login forms so if you visit a phishing site, the password manager will not fill in the credentials, signaling that something is not right.
- Always check a site’s URL before logging in.
Phishing sites are often made to appear more or less identical to legitimate sites so it’s not surprising that a lot of users fall for it. However, no matter how legitimate a phishing site’s design may look, the URL will always give it away. So before you try to log in anywhere, always check that the URL is as it’s supposed to be.